Pass-the-Cookie attacks let hackers bypass MFA using stolen browser cookies, putting corporate accounts at risk across Office 365, Azure, and more.
MFA works by verifying users through multiple factors, but attackers now steal session cookies—small browser files that keep users logged in.
In these attacks, hackers grab cookies like Microsoft’s ESTSAUTH, which confirms access to Office 365 services.
Once stolen, these cookies let attackers pose as legitimate users, bypassing device and location checks.
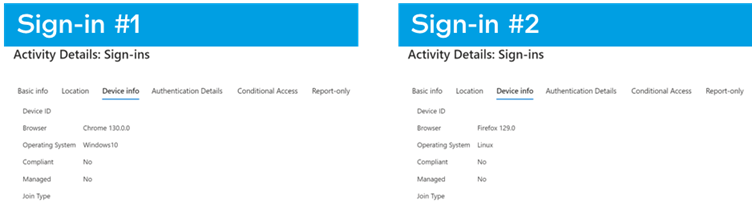
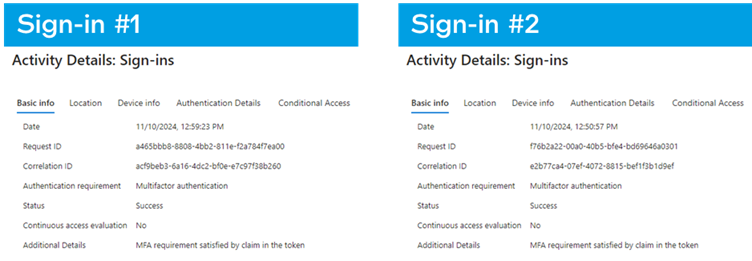
Here’s a clear example seen in Azure logs:
- Real login: User signs into Office 365 on Chrome (Windows 11) and completes MFA with Microsoft Authenticator.
- Attack: Hacker logs in using the same account on Firefox (Ubuntu) — no password or MFA needed — just using a stolen ESTSAUTH cookie.
Both events look almost identical in Azure logs, with only slight browser/OS differences.
Without advanced detection, these attacks can easily slip past standard security tools.
Cookie Hijacking Explained
Session hijacking starts when malware like LummaC2, Redline, or Racoon infects a device. These infostealers, often hidden in fake software updates, search for browser cookies and decrypt them.
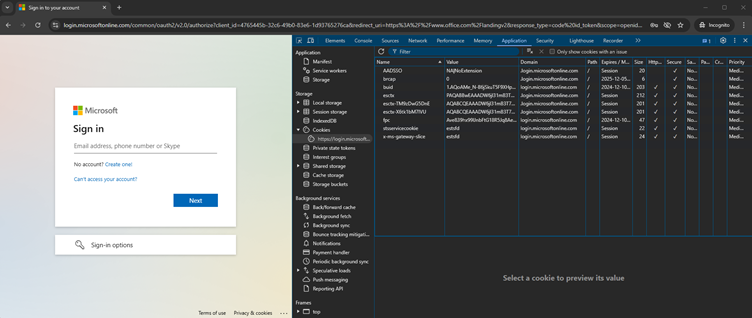
For example, LummaC2 steals ESTSAUTH cookies, which hackers inject into their own browsers using developer tools.
How It Works:
- Steal Cookie: After hacking a Windows/Chrome device, the attacker grabs the ESTSAUTH cookie from
login.microsoftonline.com. - Hijack Session: On a separate Ubuntu/Firefox device, the attacker adds the stolen cookie to the browser. A simple refresh gives full access to the victim’s Office 365 account.
Since the cookie already confirms the session, no password or MFA is required.
Microsoft notes that ESTSAUTH cookies stay valid until the user logs out or they expire, leaving accounts exposed for days or weeks if unnoticed.
As more companies adopt MFA, attackers are moving from stealing passwords (like using Mimikatz to dump LSASS) to stealing session cookies instead.
MSSPs report a 300% rise in cookie theft attacks since 2023, mainly targeting finance and healthcare.
Mitigation
To defend against Pass-the-Cookie attacks, security experts recommend:
- Monitor Sessions: Use tools like UEBA to detect unusual device or browser changes during active logins.
- Set Conditional Access: Limit logins to trusted devices and enforce extra MFA for sensitive actions.
- Protect Cookies: Shorten token lifespans and link sessions to device fingerprints using features like Azure AD’s Continuous Access Evaluation (CAE).
- Detect Infostealers: Block malware that steals credentials using strong EDR solutions and limit admin privileges on endpoints.
MFA alone isn’t enough—securing session cookies is now essential for protecting accounts.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment