
The “BMI CalculationVsn” app on the Amazon App Store secretly collects sensitive data, like app package names and SMS messages, posing a privacy risk. Its true intent appears to be data theft or other cyberattacks.
It secretly starts screen recording during user interaction, possibly capturing sensitive info like passwords. Though it doesn’t upload recordings yet, the threat suggests it is still evolving.

The app scans the device to compile a list of all installed applications, which helps it identify users as potential targets for sophisticated attacks or prepare for future attacks. It also intercepts all incoming SMS messages, which could include sensitive information like one-time passwords (OTPs) and verification codes.
This stolen data is then uploaded to a Firebase storage bucket called “testmlwr-d4dd7.appspot.com,” where it can be accessed by attackers for further exploitation.
The “com.zeeee.recordingappz” malware, initially a screen recorder, turned into an SMS-stealing app in October 2024, showing it’s still being developed and tested.
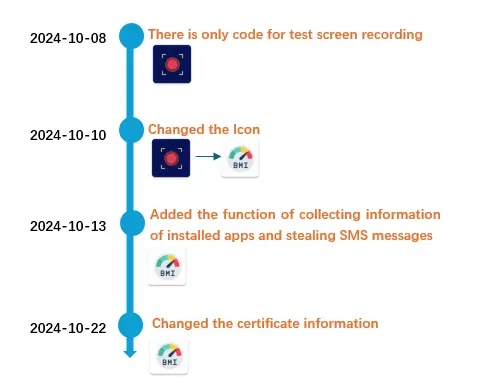
The “testmlwr” in the Firebase Installation API suggests the app is in testing.
Cybercriminals used the reputation of a legitimate Indonesian IT provider to spread the malware as a fake app on the Amazon Appstore, hinting at possible links to Indonesia.
To protect devices from malicious apps, users should install trusted antivirus software, review app permissions, and watch for unusual behavior like slow performance, battery drain, or high data usage.
McAfee warns that even harmless apps like “BMI CalculationVsn” can pose security risks. Users must stay vigilant and use strong security measures to protect their privacy.
IoC
Distribution website:
- hxxps://www.amazon.com/PT-Visionet-Data-Internasional-CalculationVsn/dp/B0DK1B7ZM5/
C2 servers/Storage buckets:
- hxxps://firebaseinstallations.googleapis.com/v1/projects/testmlwr-d4dd7
- hxxps://6708c6e38e86a8d9e42ffe93.mockapi.io/
- testmlwr-d4dd7.appspot.com
Sample Hash:
- 8477891c4631358c9f3ab57b0e795e1dcf468d94a9c6b6621f8e94a5f91a3b6a




