A major vulnerability, CVE-2024-31317, has been discovered in Android, allowing attackers to exploit the Zygote process for system-wide code execution and privilege escalation. This flaw affects devices running Android 11 or earlier, presenting a serious security risk.
All about Android Zygote Flaw
The Zygote process is a core part of Android, responsible for launching new apps and system processes. Running with system privileges, it’s a prime target for attackers aiming for elevated access.
The vulnerability stems from how the System Server handles the hidden_api_blacklist_exemptions setting, which lets some apps bypass Android’s hidden API restrictions.
The issue occurs because the System Server doesn’t properly escape newlines in this setting when passing it to Zygote, allowing attackers to inject arbitrary commands into the Zygote process.
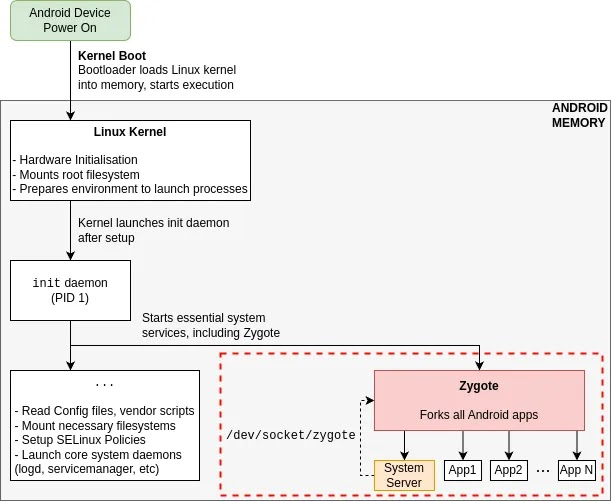
Attackers can exploit this vulnerability via the Android Debug Bridge (ADB) Shell, which has the WRITE_SECURE_SETTINGS permission to modify the hidden_api_blacklist_exemptions setting.
By injecting malicious commands, attackers can execute arbitrary code with system-wide privileges. A proof-of-concept shows how they can escalate privileges and maintain control by launching a persistent shell. Exploiting this vulnerability could cause severe issues, including device bootloops.
Mitigation Steps
To mitigate the risks, users can restore normal Zygote behavior by deleting the modified hidden_api_blacklist_exemptions setting through ADB Shell and rebooting the device. However, this will also remove any injected payloads, requiring attackers to repeat the exploitation process to regain elevated access.
This discovery highlights the importance of securing Android’s core processes and the need for quick patches to prevent such exploits.













Leave A Comment