
Transparent Tribe (aka APT36), active since 2016, uses social engineering to target Indian government and military personnel. Recently, their CapraRAT has been mimicking popular Android apps to attack Android users, showing adaptability and expanding their espionage efforts against Indian targets.
All about CapraRAT
The malware uses obfuscated URLs and WebView to open YouTube and CrazyGames[.]com. In addition, apps like “Sexy Videos” employ social engineering tactics centered on romance. Meanwhile, others, such as “TikTok” and “Weapons,” direct users to specific YouTube channels or gaming sites like CrazyGames[.]com.
SentinelLabs researchers noted that CapraRAT’s evolving tactics highlight its adaptability. By using legitimate platforms as covers for malicious activities, the malware maintains access to sensitive device permissions.
The latest CapraTube campaign continues its romance-themed social engineering through these apps, which open YouTube and perform related searches. Despite removing some previously requested permissions, the malware still demands numerous dangerous permissions during monitoring.
Targeting Android 8.0 (Oreo) and newer versions contrasts with the September 2023 campaign, thereby enhancing compatibility with modern devices. However, suspicious permissions are still requested despite these updates. As a result, a new WebView class has been added to support older Android versions, aiming to maintain functionality across different platforms.
Despite updates, CapraRAT’s core functionality, centered on surveillance, remains largely unchanged. Initiated through MainActivity and utilizing the TCHPClient class, it performs malicious activities such as audio streaming, call recording, contact logging, file browsing, and SMS sniffing. Moreover, these capabilities underscore its persistent focus on gathering sensitive information.
These variants communicate with C2 servers via specific hostnames and IP addresses, some of which are linked to threats like CrimsonRAT. Furthermore, recent updates focus on enhancing software reliability and compatibility with newer Android versions.
The malware employs social engineering tactics targeting groups like mobile gamers or firearms enthusiasts.
Users should carefully review app permissions during installation to avoid unnecessary access requests. Additionally, incident responders must vigilantly monitor network indicators and method names associated with CapraRAT.
IoCs – CapraRAT
Files
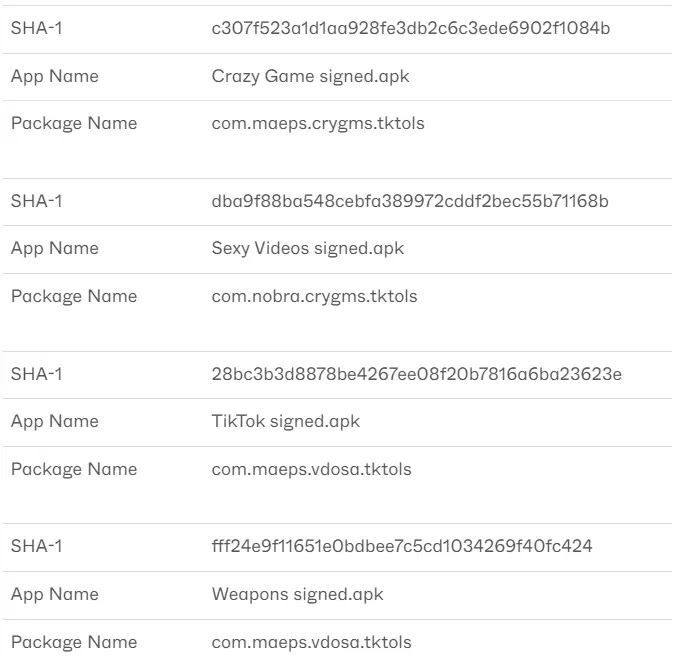
| SHA1 | Name |
| 28bc3b3d8878be4267ee08f20b7816a6ba23623e | TikTok signed.apk |
| c307f523a1d1aa928fe3db2c6c3ede6902f1084b | Crazy Game signed.apk |
| dba9f88ba548cebfa389972cddf2bec55b71168b | Sexy Videos signed.apk |
| fff24e9f11651e0bdbee7c5cd1034269f40fc424 | Weapons signed.apk |
Network Indicators
| Domain/IP | Description |
| shareboxs[.]net | C2 domain |
| 173[.]212[.]206[.]227 | Resolved C2 IP address, hosts shareboxs.net |
| 173[.]249[.]50[.]243 | Hardcoded failover C2 IP address |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




