
International cybersecurity agencies have issued a warning about APT40, a PRC state-sponsored cyber group linked to the Ministry of State Security. Based in Hainan Province, APT40 has targeted global organizations, prompting Australian authorities to release an advisory with case studies to aid cybersecurity practitioners in detecting and mitigating their attacks.
Chinese APT40
APT40 remains a persistent concern for Australian and other regional networks, swiftly adapting to exploit new vulnerabilities.
APT40 conducts regular reconnaissance to pinpoint vulnerabilities and prioritize credential theft. After compromising websites, they now focus on using SOHO devices as operational infrastructure and last-hop redirectors, resembling legitimate traffic to evade detection.
The Australian Signals Directorate’s ACSC investigated APT40’s network compromise between July and September 2022, revealing abuse of a custom web application for multiple access vectors, host enumeration, web shell usage, and sensitive data exfiltration, including privileged credentials. This incident underscores the critical need for robust network security measures and logging configurations.
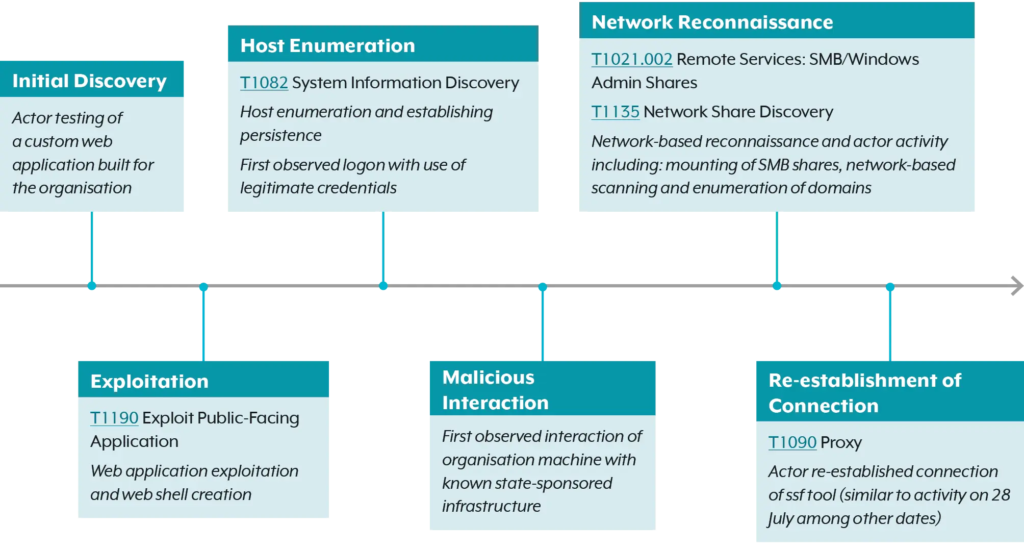
APT40 breached a network in April 2022 through a vulnerable remote access portal, deploying web shells for credential theft and potential unauthorized access. Their tactics included exploiting public-facing apps, capturing login data, and attempting lateral movement, prompting an investigation and remediation guidance from the Australian Cyber Security Centre.
Mitigation strategies include:
- Maintain comprehensive logging
- Prioritize patch management
- Implement network segmentation
- Disable unnecessary network services and ports
- Deploy web application firewalls (WAFs)
- Enforce least privilege access
- Implement multi-factor authentication (MFA) for remote access
- Upgrade outdated equipment
- Review and secure custom applications
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




