
Two Chinese language hacking teams conducting cyber espionage and stealing mental property from Japanese and western firms are deploying ransomware as a decoy.
The use of ransomware in espionage operations is to obscure their tracks and create a distraction for defenders.
The 2 clusters of hacking exercise analyzed by Secureworks are “Bronze Riverside” (APT41) and “Bronze Starlight” (APT10).
Both are utilizing the HUI Loader to deploy distant entry trojans, PlugX, Cobalt Strike, and QuasarRAT.
The configuration of Cobalt Strike beacons in three distinct assaults utilizing AtomSilo, Evening Sky, and Pandora revealed a shared C2 handle.
Moreover, the identical supply was used for importing HUI Loader samples on Virus Complete this yr.
The activity and victimology of LockFile, AtomSilo, Rook, Night Sky, and Pandora are unsual compared to financially motivated ransomware operations.
As these were targeting a small number of victims over a brief period and then abandon the project altogether.
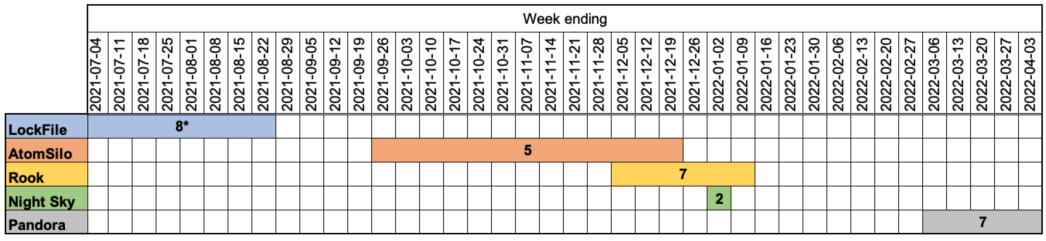
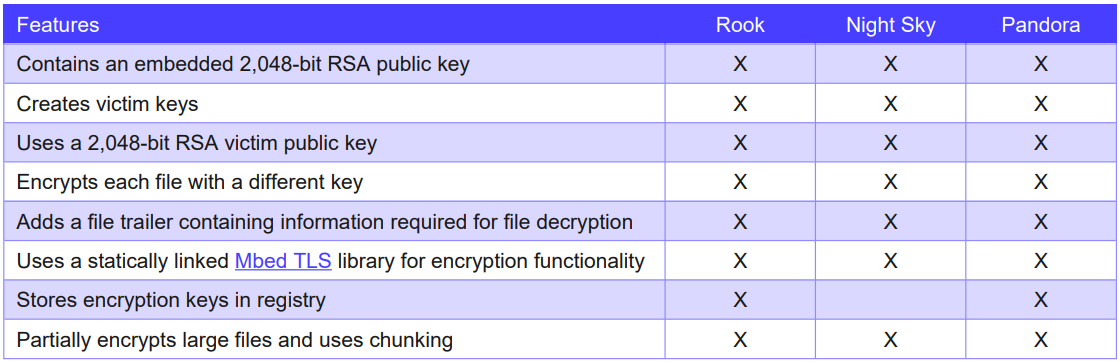
LockFile and AtomSilo also appear to be very similar, while Night Sky, Pandora, and Rook were all derived from Babuk source code and also feature extensive similarities in their code.
These five ransomware operations didn’t leave a mark in the cybercrime community and never really grew to become a significant threat. Also, they were all deserted somewhat prematurely.
Since all of the discussed ransomware strains are based on publicly available or leaked code, and Chinese threat groups are known for sharing backdoors and infrastructure, nothing can be said with certainty.
Observed File Hash
- b16bb2f910f21e2d4f6e2aa1a1ea0d8b
- a4a6abf4ed4c9447683fba729a17197b
Follow us for more, Facebook, Twitter, LinkedIn and Instagram





