
Hackers exploit weaponized shortcut files because they can execute malicious code without targeting specific users.
Given their widespread usage and familiarity, shortcut files offer an effective platform for deploying malware.
The utilization of seemingly harmless shortcuts is a prime method for hackers to circumvent security checks and render victims’ systems vulnerable.
ASEC cybersecurity researchers recently unearthed hackers’ active exploitation of weaponized shortcut files to disseminate CHM malware.
All About CHM malware
AhnLab uncovered a Korean CHM malware stealing user data and targeting Korean entities. This aligns with the actor’s pattern of distributing malware in various formats like LNK, DOC, and OneNote.
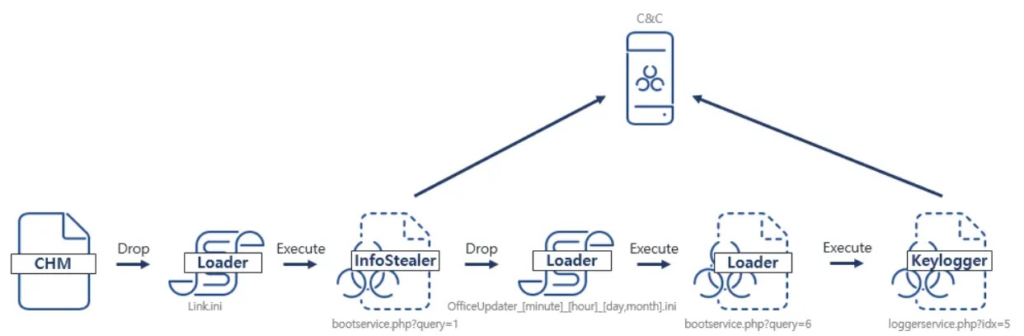
While the overall execution flow still depends on multiple scripts for stealing user information and keylogger data, recent samples exhibit slight variations in their operation.
Previously, this group’s malicious objects often masqueraded as HWP documents or resembled compensation forms, North Korea-related surveys, or press releases on various topics.
Upon executing the CHM file, a help file is displayed, while a malicious script runs concurrently, creating and launching Link.ini in “%USERPROFILE%\Links”.
The Link.ini connects to a URL (changed from “list.php?query=1” to “bootservice.php?query=1”) hosting a Base64 encoded script. Once decoded, this script, previously analyzed, exfiltrates user data, generates a malicious script file, and registers it as a service under “%USERPROFILE%\AppData\Local\Microsoft\Windows\Temporary Internet Files\OfficeUpdater_[time].ini”. It’s set to run automatically every 60 minutes.
Below, we’ve listed all types of exfiltrated information:
- System Information
- List of Files in the Folder
- Information on Currently Running Processes
- Anti-malware Information (Code Only, Not Executed)
The periodically running service connects to a URL running a Base64 encoded malicious script, with “list.php?query=6” changed to “bootservice.php?query=6”.
This exposes an encoded script utilizing PowerShell to access another URL with “InfoKey” and encoded data as parameters.
The PowerShell script on the URL decodes and executes an obfuscated secure string payload.
Attackers are employing sophisticated obfuscation methods surpassing simpler deobfuscation techniques, making it challenging for readily available detectors to detect their activities.
The final decoded payload conducts keylogging, storing captured keystrokes and clipboard data in ‘%APPDATA%\Microsoft\Windows\Templates\Office_Config.xml’ before transmitting it to the attacker’s server and deleting the file.
While the attack’s general execution isn’t novel, recent samples exhibit significantly more intricate obfuscation methods, indicating potential advancements in evasion techniques by a single group responsible for previous campaigns.
Given that this malware exclusively targets Korean users, they should exercise extra caution when opening files from untrusted or suspicious sources.
IOC
- b2c74dbf20824477c3e139b48833041b
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




