
Choicejacking is a new USB attack that tricks phones into sharing data at public charging stations, bypassing security prompts in milliseconds.
If you believed using a public phone charger was safe, it’s time to reconsider. Despite multiple updates designed to protect smartphones from “juice jacking” attacks, cybersecurity experts have uncovered a new threat that bypasses these protections. A recent study reveals that attackers are now using a technique called “Choicejacking” to gain unauthorized access to smartphones, often without the user even noticing.
From Juice Jacking to Choicejacking:
A New Threat to Your Smartphone Security.
While “juice jacking” has long been a known risk when using public phone chargers, a new form of attack has emerged: “Choicejacking.” This latest cybersecurity threat bypasses the protections put in place to safeguard your phone, exploiting unsuspecting users to gain unauthorized access, often without any visible signs of tampering.
How Choicejacking Operates:
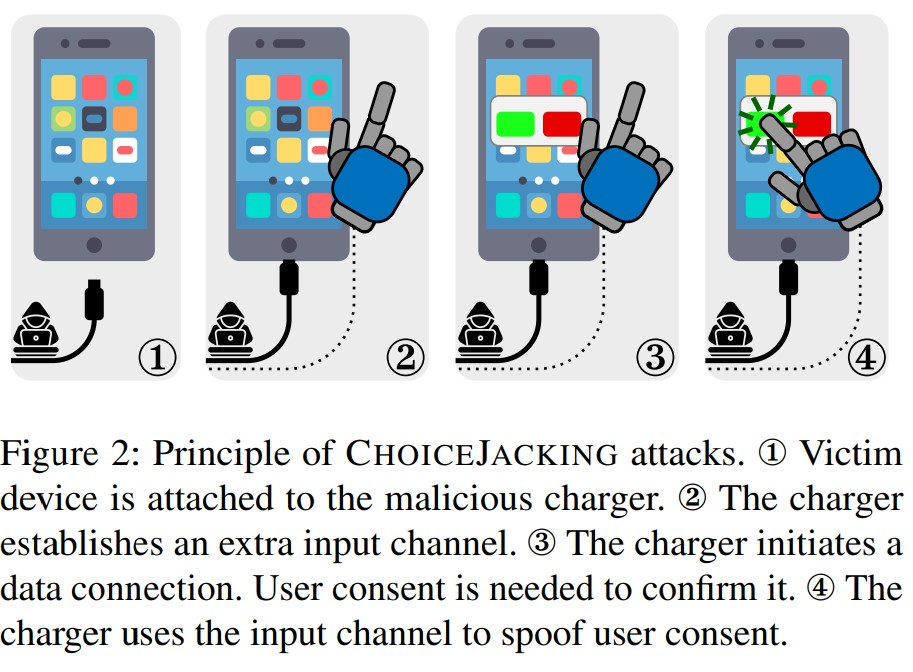
Instead of using traditional malware, this attack exploits USB or Bluetooth input devices to mimic user actions. A compromised charging station can simulate keyboard inputs, overflow input buffers, or manipulate device communication protocols, stealthily switching your phone into data-transfer or debug mode.
The entire process happens in under 133 milliseconds—quicker than the blink of an eye—meaning the phone reacts before you even notice.
Adrianus Warmenhoven, a cybersecurity advisor at NordVPN, explains that the real danger lies in the illusion of control. “Choicejacking is especially dangerous because it tricks the device into making decisions the user never intended, all without them realizing it,” he said.
Once the attacker gains access, they can silently browse photos, read messages, or install malicious software.
Public Ports Aren’t Worth the Risk:
The rise of Choicejacking underscores what cybersecurity experts have been warning for years: public USB ports are not safe. Whether you’re at airports, hotels, or cafés, a compromised charging station could be lurking, ready to hijack your device.
Warmenhoven cautions, “With just one misleading prompt, attackers can trick users into enabling data transfer, putting personal files and sensitive information at risk.”
This threat affects both Android and iOS users. While some platforms may offer more obvious prompts or charge-only options, the core vulnerabilities remain, and cybercriminals are always finding ways to bypass these safeguards.
How to Protect Yourself:
Researchers recommend keeping your phone’s software up to date and avoiding unfamiliar charging ports whenever possible. Preparation is key—carrying a portable power bank is an easy way to stay in control while on the go. If you must plug in, opt for a wall outlet with your own cable and adapter rather than using a public USB port, especially those that seem suspicious or overly complex.
Some devices offer a “charge only” mode, which blocks any data transfer. If your phone has this option, make sure to enable it. While attackers continuously come up with new methods, staying vigilant and informed is your best defense.




