
McAfee Labs researchers have identified a sophisticated malware delivery method, “ClickFix,” using advanced social engineering to trick users into executing malicious scripts, leading to severe security breaches. This article explores the intricacies of ClickFix, its implications, and protective measures.
All about ClickFix
The ClickFix infection chain starts by luring users to seemingly legitimate but compromised websites. These sites redirect victims to domains with fake popups, instructing them to paste a script into a PowerShell terminal.
Once the script is executed in the PowerShell terminal, the malware infiltrates the victim’s system, leading to data theft, system compromise, or further malware propagation.
This method’s sophistication lies in exploiting users’ trust in seemingly authentic websites and prompts.
Two notable malware families, Lumma Stealer and DarkGate, have been leveraging the ClickFix technique.
Lumma Stealer extracts sensitive information like passwords and credit card details from infected systems. DarkGate is more advanced, providing remote access, establishing persistent backdoors, and using evasion tactics to avoid detection. This combination of malware and the ClickFix technique poses a significant challenge for cybersecurity professionals.
The Impact of Phishing Emails
McAfee Labs identified a phishing email with an HTML attachment posing as a Word document. These emails are pivotal in the ClickFix infection chain, using error prompts to trick users into downloading and executing malicious software.
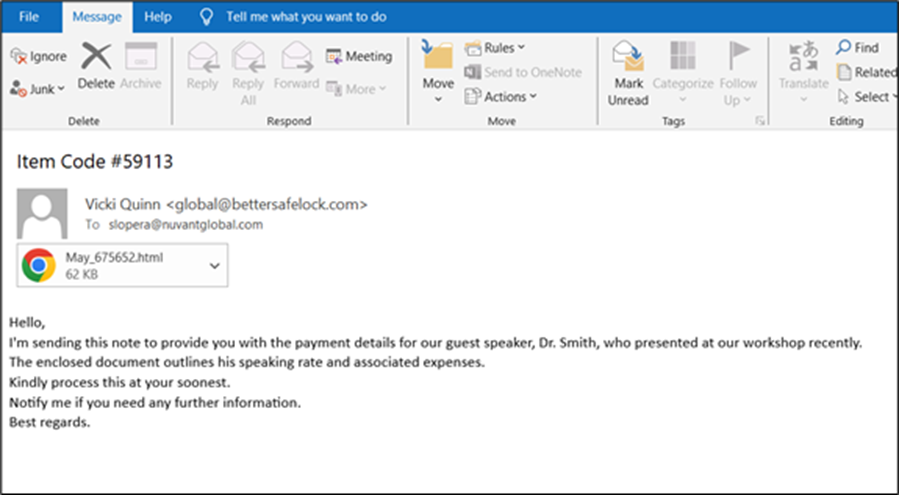
The phishing email tactic is effective because it exploits users’ familiarity with common file types and error messages, presenting a seemingly legitimate problem and solution to increase the likelihood of executing the malicious script.
Upon examining the HTML attachment’s code, researchers found several base64-encoded content blocks containing the malicious script. Users were instructed to paste this script into their PowerShell terminal, which, once executed, initiates the malware download and installation process.
Encoding and disguising the malicious script within encoded blocks highlights the attackers’ sophistication, making it more difficult for automated security systems to detect and block the threat.
To defend against the ClickFix infection chain and similar threats, consider these precautions:
- Verify Email Sources: Confirm the sender’s identity before opening unexpected attachments or emails from unknown sources.
- Avoid Script Pasting: Refrain from pasting scripts or commands from untrusted sources into your terminal or command prompt.
- Update Security Tools: Keep your security software current to detect and block advanced threats effectively.
- Stay Informed: Stay updated on cybersecurity threats and educate others on best practices for online safety.
IoCs
| File | SHA256 |
| DarkGate | |
| c5545d28faee14ed94d650bda28124743e2d7dacdefc8bf4ec5fc76f61756df3 | |
| Html | 0db16db812cb9a43d5946911501ee8c0f1e3249fb6a5e45ae11cef0dddbe4889 |
| HTA | 5c204217d48f2565990dfdf2269c26113bd14c204484d8f466fb873312da80cf |
| PS | e9ad648589aa3e15ce61c6a3be4fc98429581be738792ed17a713b4980c9a4a2 |
| ZIP | 8c382d51459b91b7f74b23fbad7dd2e8c818961561603c8f6614edc9bb1637d1 |
| AutoIT script | 7d8a4aa184eb350f4be8706afb0d7527fca40c4667ab0491217b9e1e9d0f9c81 |
| Lumma Stealer | |
| URL | tuchinehd[.]com |
| PS | 07594ba29d456e140a171cba12d8d9a2db8405755b81da063a425b1a8b50d073 |
| ZIP | 6608aeae3695b739311a47c63358d0f9dbe5710bd0073042629f8d9c1df905a8 |
| EXE | e60d911f2ef120ed782449f1136c23ddf0c1c81f7479c5ce31ed6dcea6f6adf9 |




