
In recent months, security researchers have identified a new phishing campaign aimed at macOS users, disguised as a CAPTCHA verification process.
Known as “ClickFix,” this attack combines social engineering with OS detection to trick victims into running malicious commands directly in their terminals.
By imitating legitimate Cloudflare-style verification checks, the malware bypasses the use of traditional binaries. Instead, it relies on base64-encoded scripts that retrieve and execute an obfuscated AppleScript payload.
When unsuspecting users visit a compromised URL—typically posing as well-known trading platforms—they are greeted with a human verification page customized for their operating system.
Windows users are shown harmless-looking PowerShell instructions, while macOS users are prompted to open Terminal, paste a copied command, and hit Return.
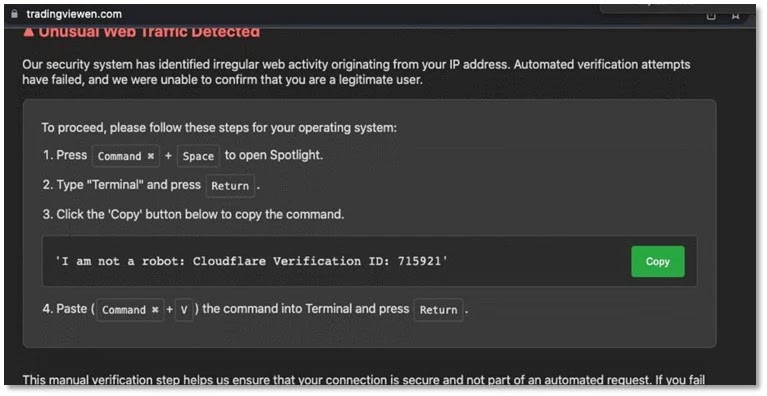
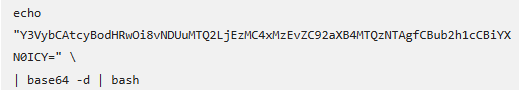
Forcepoint analysts discovered that this slight difference in instructions is strategically crafted to deceive macOS users into running a command that decodes and pipes a base64-encoded string into bash.
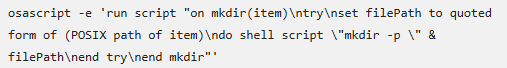
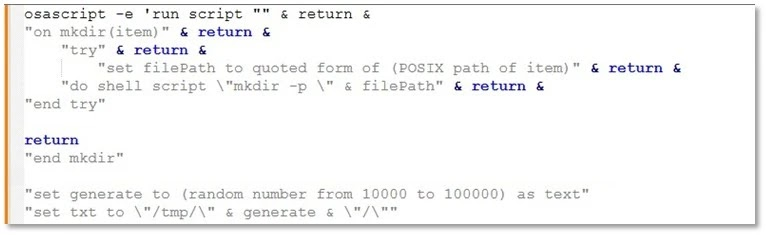
Once the command is executed, it installs an obfuscated AppleScript compiled file (.scpt), which performs the primary data-harvesting tasks. The script starts by creating a unique temporary directory in the /tmp folder, using osascript calls to assemble and run additional commands.
Forcepoint researchers observed that, after setting up the directory, the malware scans the user’s Desktop, Documents, and Library folders for files with extensions like .pdf, .docx, .key, as well as browser-related artifacts such as Keychain databases, Safari cookies, and Apple Notes databases.
The script proceeds to enumerate profiles in Firefox and Chromium-based browsers, copying saved credentials, cookies, form history, and encrypted wallet files for known crypto extensions like MetaMask and Exodus.
Infection Mechanism Deep Dive
The infection process relies on the manual execution of what appears to be a harmless “verification” command. By using base64 encoding, the attackers conceal the true intent of the payload, effectively bypassing signature-based detection.
Once decoded, the payload retrieves a heavily obfuscated AppleScript from a remote server (hxxp://45.146.130[.]131/d/vipx14350). This AppleScript uses random string obfuscation and nested osascript calls to complicate static analysis efforts.
Upon execution, it prompts the user for their password to escalate privileges and then collects system profile details via:-
The harvested data, along with gathered files, is archived into /tmp/out.zip and exfiltrated to the attacker’s C2 endpoint at 45.146.130.131/log.
A cleanup routine then removes the temporary directory to erase traces, complicating forensic recovery.
By blending familiar CAPTCHA prompts with terminal-based social engineering, the ClickFix malware—specifically the Odyssey stealer—showcases a sophisticated evasion method that bypasses traditional antivirus defenses. This highlights the critical need for increased user awareness and the implementation of multi-layered endpoint security measures.




