
Researchers uncovered an advanced cyberattack involving a dormant Python Package Index (PyPI) package called Django-log-tracker, which was unexpectedly updated to distribute the NovaSentinel stealer malware.
This finding underscores a substantial threat to the software supply chain, underscoring the imperative for developers and organizations to bolster their security measures.
Compromised PyPI Package Deploys NovaSentinel Stealer
The django-log-tracker package, initially published in April 2022, remained inactive until a suspicious update on February 21, 2024, caught Phylum’s attention.
The deviation of the update from the GitHub repository’s activity indicated a potential compromise of the developer’s PyPI account. This incident underscores a worrying pattern of attackers exploiting inactive packages to carry out supply chain attacks.
The malevolent update stripped the package down to its core components, retaining only an init.py and example.py file, both housing identical malicious code.
Four sites on VirusTotal flagged the executable as hazardous. Upon closer examination, it appears to be an NSIS launcher, facilitating easy extraction of the binary’s data. Further inspection reveals the presence of an Electron application within.
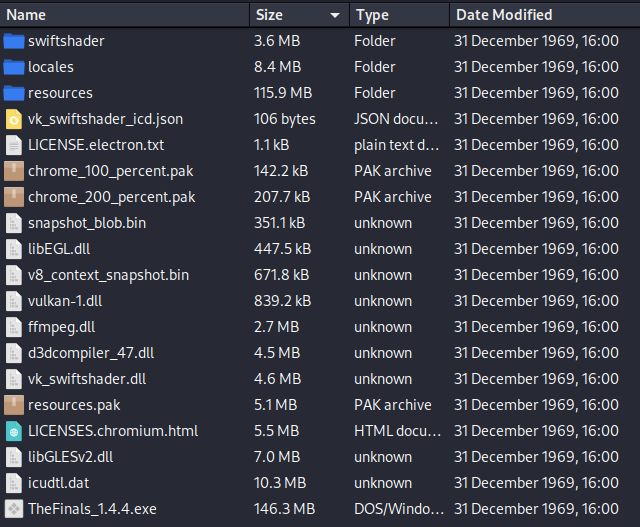
Upon execution, this code initiates the download and execution of an executable titled “Updater_1.4.4_x64.exe” from a remote server. This executable harbors the NovaSentinel stealer malware on Windows, renowned for its capacity to extract sensitive information from compromised systems.
NovaSentinel, initially documented by Sekoia in November 2023, has been disseminated via counterfeit Electron applications on websites providing video game downloads. This recent compromise of a PyPI package signifies an endeavor at a supply chain attack, exploiting the trust inherent within the developer community to propagate malware.
The django-log-tracker package had garnered 3,866 downloads, while the rogue version 1.0.4 was downloaded 107 times on the day of its release. Phylum’s swift detection and reporting prompted the removal of the package from PyPI, halting further downloads and mitigating the risk of potential infections.
Phylum’s discovery emphasizes the critical need for vigilance and the adoption of strong security measures when interacting with third-party packages. Developers and organizations are urged to thoroughly review package updates, particularly those from inactive projects, and to utilize automated security tools capable of identifying abnormal behaviors.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




