
Hackers target SMBs because they often have weaker security and lack cybersecurity awareness. Without regular security audits or incident response plans, SMBs become easy targets for attackers exploiting vulnerabilities.
CosmicBeetle
ESET researchers confirmed that the CosmicBeetle group has been deploying ScRansom ransomware worldwide.
ScRansom is Delphi-based malware targeting SMBs across various industries by exploiting vulnerabilities such as:
- EternalBlue (CVE-2017-0144)
- Zerologon (CVE-2020-1472)
- Others (CVE-2023-27532, CVE-2021-42278, CVE-2021-42287, CVE-2022-42475)
It uses advanced encryption like AES-CTR-128 for file encryption, with an RSA-1024 key pair and a hardcoded RSA public key for key management.
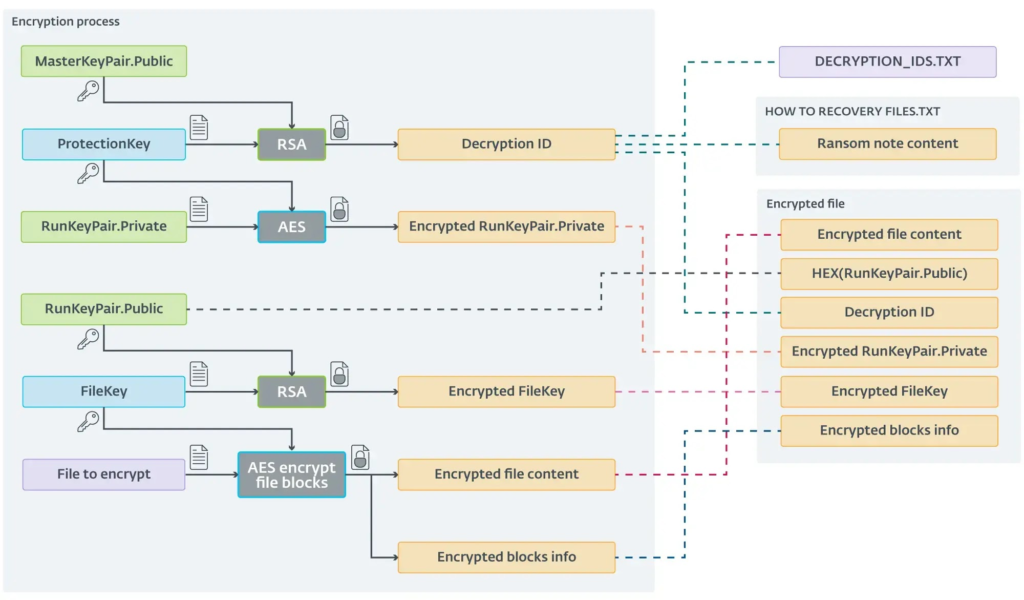
It partially encrypts files by extension, adds a “Decryption ID,” and renames them with a “.Encrypted” extension. The malware has five encryption modes: “FAST,” “FASTEST,” “SLOW,” “FULL,” and “ERASE,” the last of which makes files unrecoverable.
ScRansom shuts down specific processes and services, and its GUI includes debugging features.
CosmicBeetle has impersonated LockBit using its leaked builder and may be linked to RansomHub.
The group’s tools include ScHackTool, ScInstaller, ScService, ScPatcher, and ScKill for process termination.
They communicate with victims via email and qTox (Tox protocol for encrypted messaging). ScRansom’s decryption is slow and prone to errors, unlike more established ransomware.
When infected, victims must collect multiple Decryption IDs and get corresponding “ProtectionKeys” from the attacker. The decryptor lacks the MasterKeyPair.Private key, relying only on these ProtectionKeys.
Victims must manually run the decryptor on each device and enter the correct ProtectionKey for each Decryption ID. The process becomes more complex if “ScRansom” runs multiple times, creating additional IDs.
The ERASE encryption mode can permanently destroy files. In one case, a victim with 31 Decryption IDs couldn’t fully recover their data, likely due to missing IDs, incomplete key provision, or file destruction.
Unlike sophisticated ransomware like LockBit Black, which provides a single decryption executable, CosmicBeetle’s method is more complex, lowering the chances of successful decryption and data recovery, even after paying the ransom.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




