
A critical vulnerability (CVE-2024-5932) in the GiveWP plugin exposes over 100,000 WordPress sites to remote code execution (RCE) attacks, as disclosed by researcher villu164 through the Wordfence Bug Bounty Program.
CVE-2024-5932
PHP Object Injection occurs when user input is deserialized into PHP objects without proper validation, allowing attackers to inject malicious objects that can execute arbitrary code or perform unauthorized actions.
The GiveWP plugin, including version 3.14.1, is vulnerable to PHP Object Injection via the ‘give_title’ parameter, allowing unauthenticated attackers to execute code and delete files.
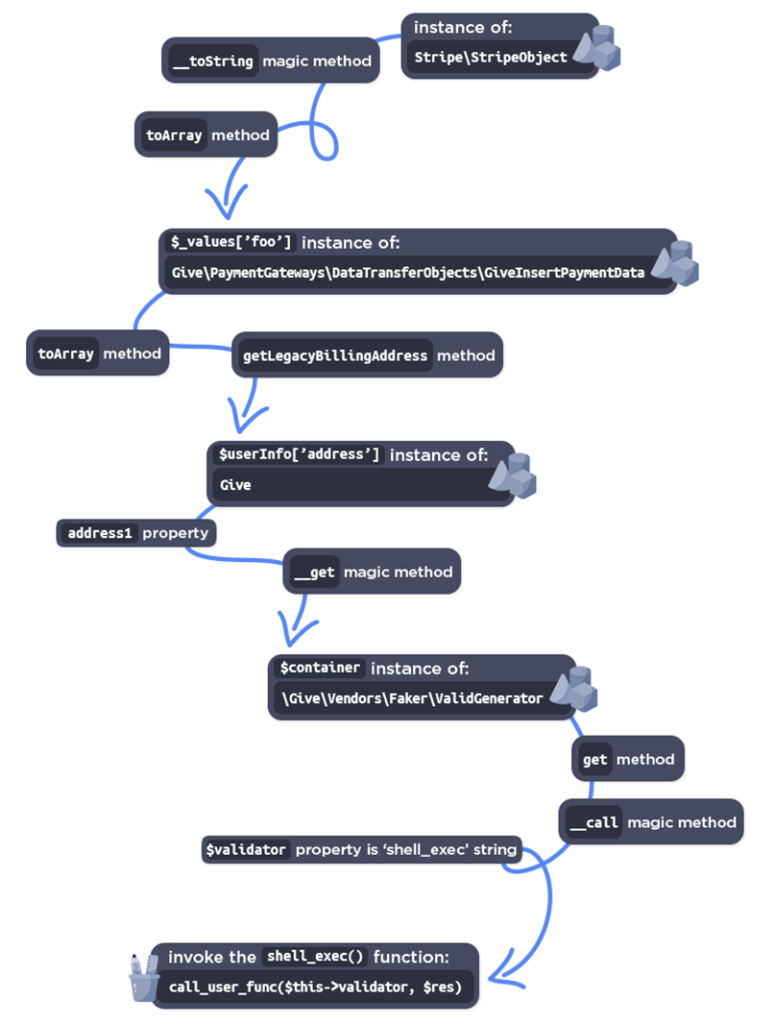
The vulnerability in the give_process_donation_form() function fails to validate the ‘give_title’ parameter, allowing attackers to inject serialized objects. This can lead to arbitrary code execution and deletion of critical files like wp-config.php, potentially compromising the site.
The vulnerability uses a POP chain involving the GiveInsertPaymentData and Give\Vendors\Faker\ValidGenerator classes to exploit shell_exec(), allowing attackers to run arbitrary commands.
CVE Details:
- ID: CVE-2024-5932
- CVSS Score: 10.0 (Critical)
- Affected Versions: <= 3.14.1
- Patched Version: 3.14.2
Response and Mitigation:
- Report Date: June 13, 2024, to StellarWP team.
- Escalation: July 6, 2024, to WordPress.org Security Team due to lack of response.
- Patch Release: August 7, 2024, in GiveWP plugin version 3.14.2.
- Action Required: Users should update to version 3.14.2 to safeguard against the vulnerability.
- Best Practices: Regular updates and security audits are recommended to keep WordPress sites secure.
- Significance: The issue underscores the importance of rigorous security practices and responsible disclosure.
- Ongoing Vigilance: Users are encouraged to remain proactive in protecting their digital assets.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




