A recently detected malspam campaign has been identified as distributing a readily available malware known as DarkGate.
DarkGate malware
“In a report published last week, Telekom Security stated that the current surge in DarkGate malware activity holds credibility due to the recent initiation of renting the malware to a restricted group of affiliates,” according to the report.
The most recent report is founded upon recent discoveries by security researcher Igal Lytzki. Lytzki delved into a “high-volume campaign” that capitalizes on compromised email threads to deceive recipients into downloading the malware.
The assault commences with a phishing URL that, upon being clicked, navigates through a traffic routing system (TDS) to deliver the victim an MSI payload contingent on specific conditions. These conditions encompass the presence of a refresh header in the HTTP response.
Running the MSI file initiates a multi-phase sequence, involving the utilization of an AutoIt script. This script facilitates the execution of shellcode, which functions as a pathway for decrypting and activating DarkGate using a crypter (or loader).
To elaborate, the loader’s purpose is to dissect the AutoIt script with precision, extracting the encrypted malware specimen embedded within.
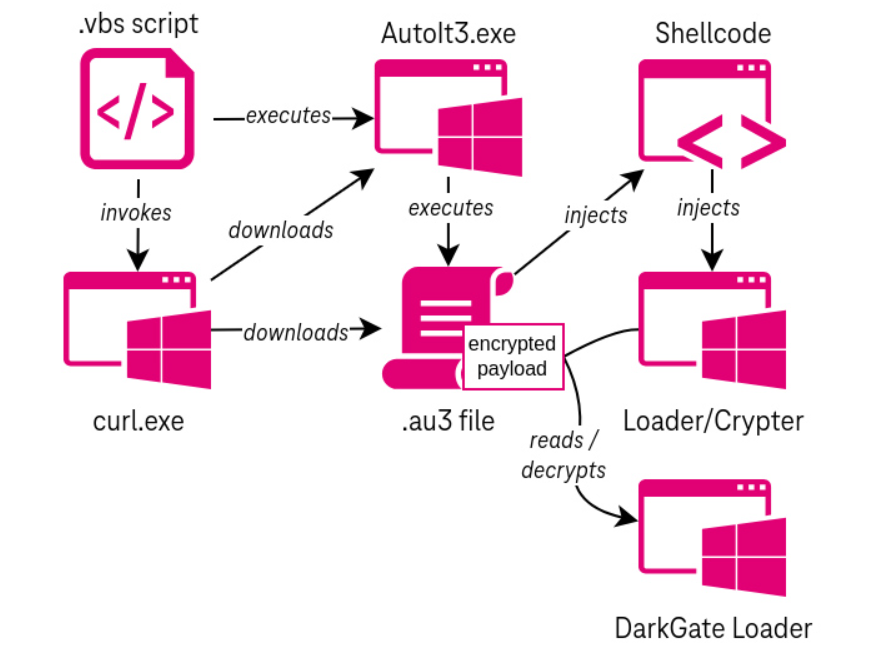
A different attack variation involves a Visual Basic Script instead of an MSI file. This script leverages cURL to fetch the AutoIt executable and script file. The specific delivery mechanism of the VB Script remains undisclosed.
DarkGate, primarily sold on underground forums by an individual known as RastaFarEye, boasts evasion features against security software, establishes persistence via Windows Registry modifications, elevates privileges, and conducts data theft from web browsers as well as applications like Discord and FileZilla.
Moreover, it connects to a control and command server (C2) for tasks like listing files, exporting data, initiating cryptocurrency miners, remote screenshots, and executing various commands.
The malware is available through a subscription, starting at $1,000 per day, escalating to $15,000 per month, and reaching $100,000 per year. The creator markets it as the “ultimate tool for pentesters/redteamers” with unique features. Notably, earlier versions of DarkGate also included a ransomware module.
Phishing attacks are a significant pathway for delivering stealers, trojans, and malware loaders like KrakenKeylogger, QakBot, Raccoon Stealer, SmokeLoader, and more. Threat actors consistently integrate new features and improvements to broaden their capabilities.
According to a recent report published by HP Wolf Security, email remained the leading vehicle for delivering malware to endpoints, accounting for 79% of threats detected in the second quarter of 2023.
IoCs
DarkGate C2 servers
149.248.0.82
179.60.149.3
185.143.223.64
185.8.106.231
45.89.65.198
5.34.178.21
80.66.88.145
89.248.193.66
a-1bcdn.com
avayacloud.com.global.prod.fastly.net
drkgatevservicceoffice.net
intranet.mcasavaya.com
onlysportsfitnessam.com
reactervnamnat.com
sanibroadbandcommunicton.duckdns.org
xfirecovery.pro













Leave A Comment