In 2025, a new wave of DCRat backdoor attacks has emerged, using the Malware-as-a-Service (MaaS) model. Cybercriminals behind this campaign distribute the malware and offer technical support and infrastructure for hosting command-and-control (C2) servers. This resurgence shows the increasing sophistication of cybercrime targeting unsuspecting users.
DCRat Malware
The attackers are using YouTube to distribute the DCRat Trojan. They either create fake accounts or hijack existing ones to upload videos promoting cheats, cracks, and gaming bots.
These videos include download links that lead to password-protected archives on legitimate file-sharing platforms.
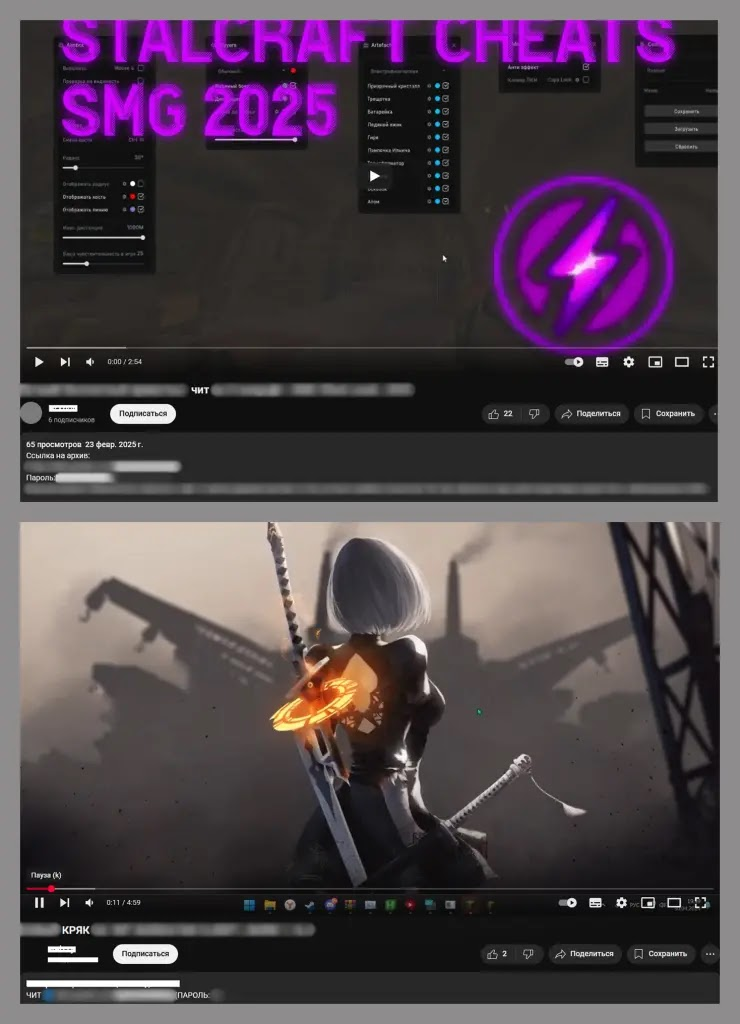
However, instead of the promised software, the archives contain the DCRat Trojan, disguised with junk files to mislead users. This tactic targets gamers and tech enthusiasts looking for free or pirated software.
DCRat, active since 2018, is a remote access Trojan (RAT) that provides backdoor access and can load plugins to enhance its features.
Analysts have identified 34 plugins, enabling capabilities like keystroke logging, webcam access, file theft, and password exfiltration.
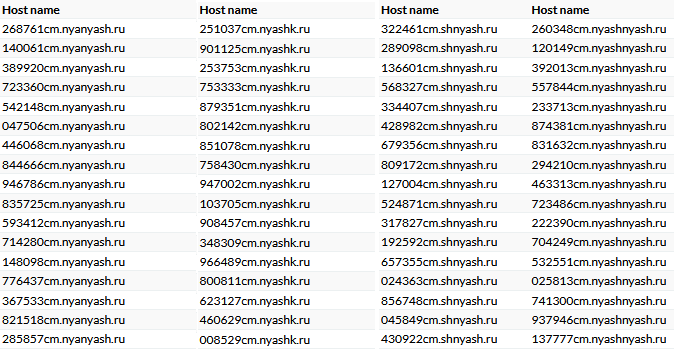
The attackers have built a vast infrastructure by registering second-level domains, mainly in the “.ru” zone, and creating third-level domains to host C2 servers. Since 2025, they’ve registered at least 57 new second-level domains, some with over 40 third-level domains.
Data shows 80% of DCRat infections are in Russia, with smaller numbers in Belarus, Kazakhstan, and China.
The attackers use culturally specific slang, like “nyashka” and “nyashtyan,” in their domain names, possibly to appeal to certain groups or hide their malicious intent.
Recommendations
Kaspersky security products have detected these DCRat samples as Backdoor.MSIL.DCRat.
This campaign highlights the growing use of password-protected archives by cybercriminals to distribute malware such as stealers, miners, and loaders.
To stay secure, users should only download game-related software from trusted sources and avoid suspicious links on platforms like YouTube.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!













Leave A Comment