
A new version of the DDoSia attack tool has been released by the threat actors, featuring an updated mechanism for obtaining the list of targets. This enhancement enables the tool to bombard the targets with spam HTTP requests, aiming to disrupt their services.
New Version of DDoSia Attack Tool
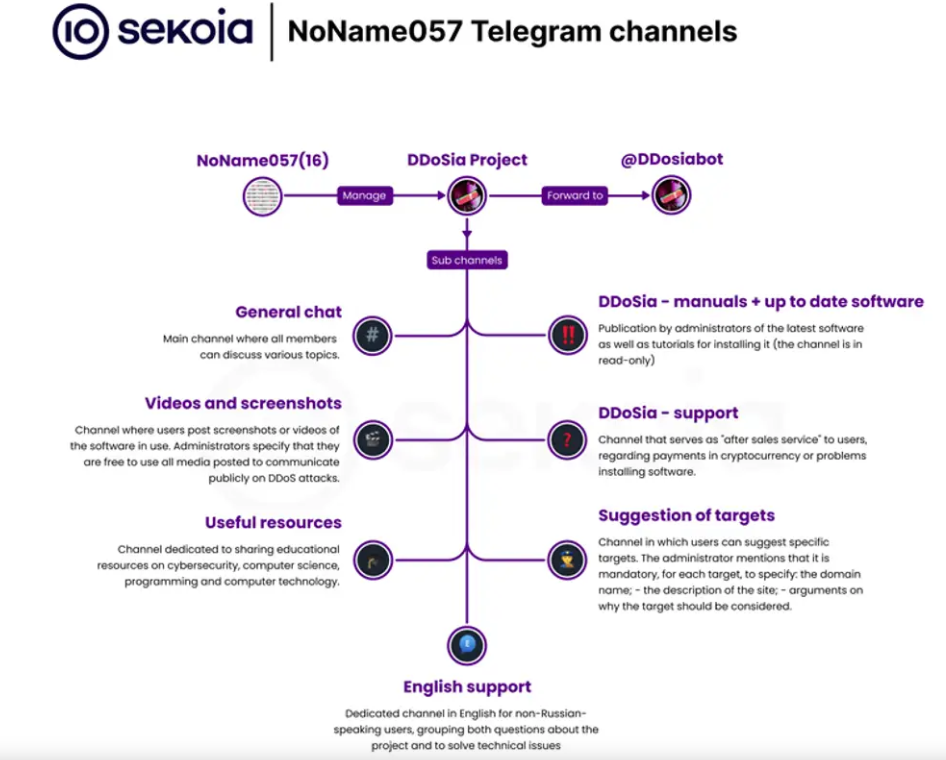
DDoSia, believed to be developed by the pro-Russian hacker group NoName(057)16, first surfaced in 2022 as the successor to the Bobik botnet. This attack tool focuses on targeting entities primarily situated in Europe, along with Australia, Canada, and Japan.
Between May 8 and June 26, 2023, the countries most significantly affected by DDoSia were Lithuania, Ukraine, Poland, Italy, Czechia, Denmark, Latvia, France, the U.K., and Switzerland, resulting in a total of 486 websites being impacted.
DDoSia is a cross-platform program, capable of running on Windows, Linux, and macOS systems, with implementations in Python and Go. The tool operates by repeatedly issuing network requests, following instructions from a configuration file received from a command-and-control (C2) server.
The most recent iteration of DDoSia incorporates encryption to obfuscate the target list, signaling continuous maintenance and development by the operators. Sekoia emphasized that NoName(057)16 is actively striving to enhance compatibility across various operating systems, implying a wider range of potential targets.
The introduction of the latest version of the DDoSia tool aligns with a cautionary statement issued by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) regarding deliberate denial-of-service (DoS) and DDoS attacks aimed at numerous organizations spanning different sectors.
These types of attacks have the potential to cause substantial disruptions, resulting in financial implications and reputational harm.
IOCS
IOCS detected by Sekoia:
| IoC Name | Info | SHA256 sum |
| d_linux_amd64 | DDoSia malware | 761075da6b30bb2bcbb5727420e86895b79f7f6f5cebdf90ec6ca85feb78e926 |
| d_linux_arm | DDoSia malware | fae9b6df2987b25d52a95d3e2572ea578f3599be88920c64fd2de09d1703890a |
| d_mac_amd64 | DDoSia malware | 8e1769763253594e32f2ade0f1c7bd139205275054c9f5e57fefd8142c75441f |
| d_mac_arm64 | DDoSia malware | 9a1f1c491274cf5e1ecce2f77c1273aafc43440c9a27ec17d63fa21a89e91715 |
| d_windows_amd64.exe | DDoSia malware | 726c2c2b35cb1adbe59039193030f23e552a28226ecf0b175ec5eba9dbcd336e |
| d_windows_arm64.exe | DDoSia malware | 7e12ec75f0f2324464d473128ae04d447d497c2da46c1ae699d8163080817d38 |
| 94[.]140.114.239 | DDoSia C2 | N/A |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




