
Evasive Panda deployed a new C# tool, CloudScout, in early 2023 to target a Taiwanese government entity. CloudScout uses modules to hijack web sessions, accessing services like Google Drive, Gmail, and Outlook by stealing browser cookies to bypass 2FA and IP tracking.
Recent security updates, such as Device Bound Session Credentials and App-Bound Encryption, may reduce the impact of this technique.
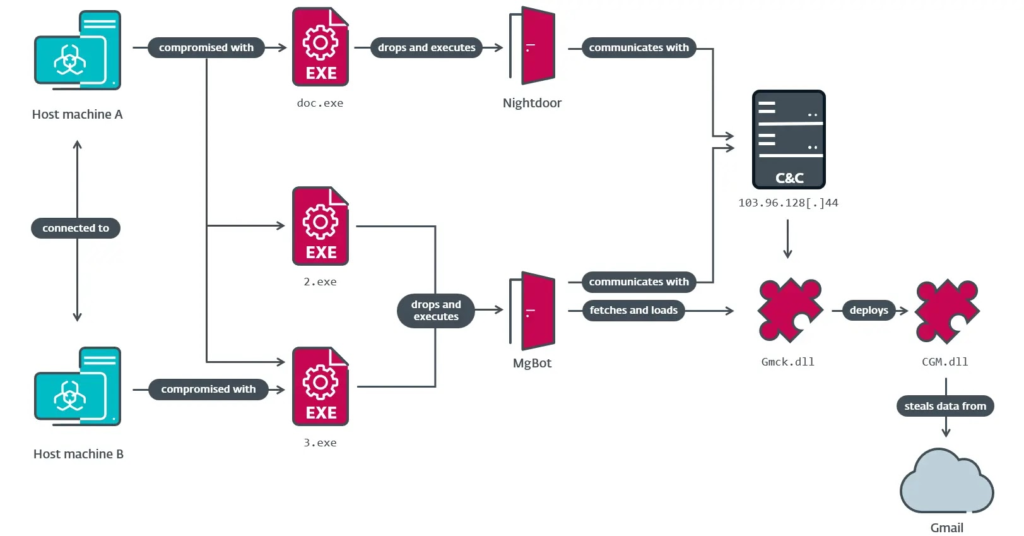
CloudScout, a malicious tool, was used in two Taiwan cyberattacks: in 2022, on a religious institution via the MgBot botnet, and in 2023, on a suspected government entity along with the Nightdoor implant.
Both incidents suggest targeted attacks on Taiwan, shown by the malware’s Taipei Standard Time and Chinese language settings. Evasive Panda developed the CloudScout .NET malware around 2020, targeting cloud services like Google Drive, Gmail, and Outlook.
The CloudScout framework includes modules targeting platforms like Twitter and Facebook, with its core, CommonUtilities, frequently updated. Attackers deploy modules selectively, showing a targeted approach.
CloudScout’s use with Nightdoor and a new MgBot variant shows Evasive Panda’s ongoing toolkit development since 2020. The Gmck C++ MgBot plugin installs the CGM module on compromised systems, using a shared RC4 encryption key to extract browser cookies and create a config file.
The encrypted file, using the RC4 key, enables CGM to access victim accounts and download sensitive data like emails. CloudScout, a modular framework, uses JSON config files created by the MgBot plugin to start data collection cycles, holding cookie data and settings for data extraction and staging.

ESET researchers note that CommonUtilities, a key part of CloudScout, provides libraries for HTTP communication and cookie handling.
The HTTPAccess library modifies HTTP headers, while the ManagedCookie library parses and integrates cookies into HTTP requests using custom regex patterns. CloudScout modules share a common structure, with core functions managed by the Cloud namespace and each module specialized in retrieving data from specific cloud services (Gmail, Drive, Outlook) via stolen cookies.
After authenticating, modules mimic a browser using hardcoded requests to gather data like emails and files. Extracted data is tagged, encrypted, compressed, and exfiltrated before modules clean up and await new configurations for the next cycle.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




