
Attackers target online shoppers using fake Amazon gift cards that deliver the Dridex banking Trojan.
Holiday Gifts as Malware:
Online shoppers from the U.S and Western Europe, targeted with fake Amazon gift cards, that deliver Dridex malware.
Cybereason Nocturnus Team has been tracking down cybercrime campaigns related to the holiday season, and more specifically to online shopping.
Due to the COVID-19 pandemic situation, consumers changed their shopping habits towards doing most of their shopping online.
However, cyber-criminals sharply make consumer-focused attacks potentially even more attractive.
According to data from the recent IBM U.S. Retail Index, “the pandemic has accelerated the shift away from physical stores to digital shopping by roughly five years,” and “e-commerce is projected to grow by nearly 20% in 2020.”
As mentioned, a phishing campaign — pretend to be an Amazon gift certificate sent via email, the security firm traced.
Dridex Phishing Campaign
Dridex has been active since at least 2012, and the primary distributor is the Evil Corp cybercrime group, Cybereason notes.
Malware gangs use current events and the holidays as themes to lure people into opening malicious attachments.
In addition, Amazon gift worth $100 that users must redeem by clicking on a phishing email button.
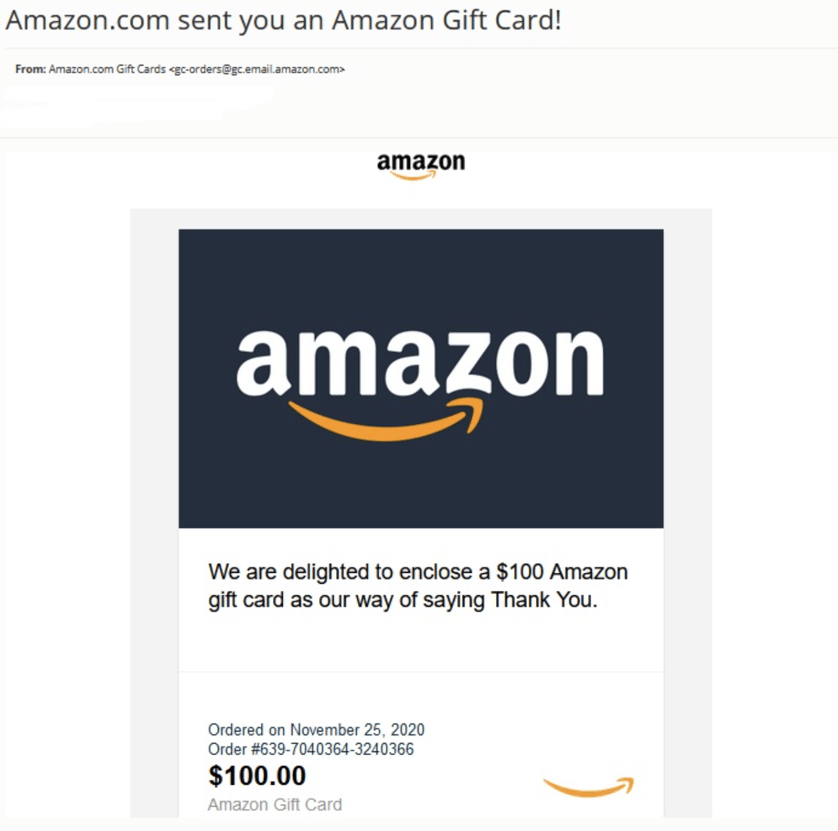
Firstly, a malicious Word document downloaded with similar names — ‘Amazon_Gift_Card,’ ‘Order_Gift_Cart,’ and ‘Amazon_eGift-Card.’ that claim to contain the gift card.
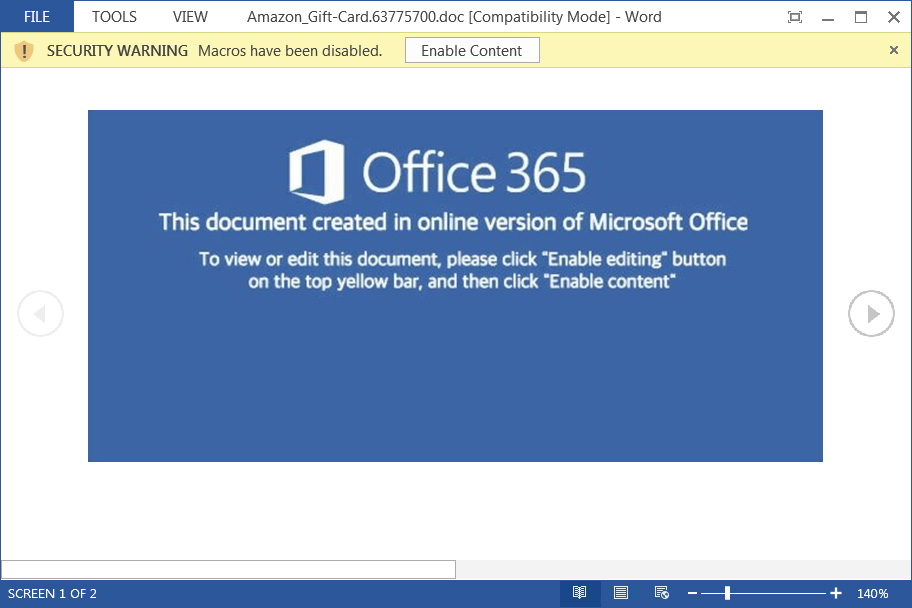
When opened, prompt to “enable content” to open the file. At this point, malicious macros downloaded and install the Dridex malware, and possibly other payloads, on the victim’s computer.
Secondly, the attackers use SCR, or screensaver, files that enable them to bypass email security.
In addition, these SCR files contain a malicious VBScript, which, when executed, unpacks the Dridex malware for exfiltrating sensitive user data, the report adds.
Security Recommendations:
Also, it is not the first time, a campaign related to Amazon used to trick victims into downloading malware.
Most Importantly, highly recommended to follow the below-mentioned security measures:
- Verify the sender by checking their Email Address
- Do not click on any links listed in the email message
- Do not open any attachments contained in a suspicious email
- Close immediately if any prompt to download and open Word documents
- Importantly, Amazon will never prompt to download a file to redeem a gift certificate.
Follow Us on: Twitter, Instagram, Facebook to get latest security news!







