
Cybercriminals are increasingly employing counterfeit browser updates that imitate genuine notifications from Google Chrome, Mozilla Firefox, and Microsoft Edge to distribute malware on victims’ computers.
Fake browser updates
A recent report by the cybersecurity firm Proofpoint unveiled that hackers operating under the codename TA569 have employed bogus update notifications to disseminate the SocGholish malware. Astonishingly, this tactic has been consistently utilized for a minimum of five years.
The group is believed to be an initial access broker, facilitating ransomware gangs to initially infiltrate networks and sell illegally obtained data.
Counterfeit browser updates involve compromised websites that present deceptive notifications mimicking official messages from browser developers like Chrome, Firefox, or Edge, indicating that an update is required, as highlighted by Proofpoint. Regrettably, when users click on these notifications, they are not downloading a genuine browser update but rather harmful malware.
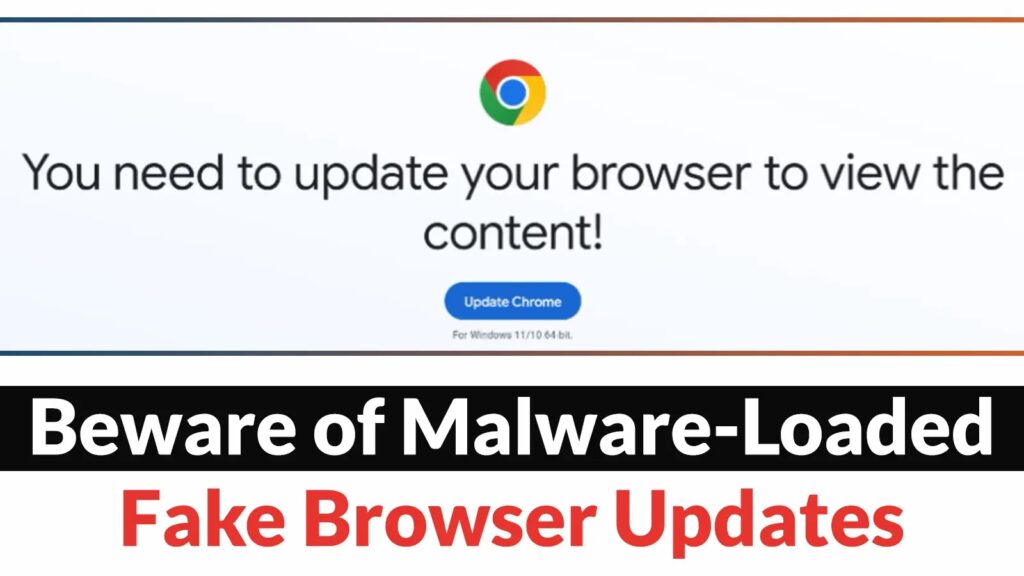
Apart from the TA569 group, additional threat actors have recently come to light employing counterfeit browser updates. Each of these malicious groups employs unique techniques to disseminate their decoy and payload, albeit primarily relying on social engineering tactics. These fake updates exploit end-users’ confidence in their web browsers and the reputable websites they frequent.
According to the researchers, they have pinpointed “at least four distinct threat groups” employing this strategy. However, it’s worth noting that these groups don’t uniformly employ the same lure to distribute their malicious payload.
Proofpoint advises fellow cybersecurity experts and stakeholders to stay updated on payload and infrastructure modifications by referring to the @monitorsg account on the Infosec Exchange platform.
Numerous users lack the knowledge and training necessary to discern and evade the deceptive ploys of attackers, making them vulnerable targets for fake browser updates.
Recommendation
- Source Verification: Only download browser updates from the official websites or trusted app stores. Avoid clicking on pop-up notifications or links from unverified sources.
- Keep Software Updated: Regularly update your browser, operating system, and security software to patch vulnerabilities that attackers may exploit.
- Security Software: Install and maintain reputable antivirus and anti-malware programs to detect and prevent malicious downloads.
- Educate and Train: Learn to recognize phishing attempts, suspicious websites, and deceptive update notifications. Educate others, such as family members and colleagues, about these risks.
- Browser Security Settings: Configure your browser’s security settings to block pop-ups and warn against potentially harmful downloads. Be cautious and selective when allowing websites to run scripts or install extensions.
IOCS
SocGholish:
C2 URI:
/editContent
8bdc4c1cd197808056e50b8b958acd380bf8a69b63aedef3f9854173c6714b32
3fb9740940d44eef823b7ff17f0274a12345a6f238cf46a1133a9e39c7b97c62
RogueRaticate:
Keitaro TDS Hosted on:
178.159.37.73
178.159.37.25
1d9900c8dbaa47d2587d08b334d483b06a39acb27f83223efc083759f1a7a4f6
08d9df800127f9fb7ff1a246346e1cf5cfef9a2521d40d6b2ab4e3614a19b772
ZPHP:
Injects lead to paths:
/cdn/wds.min.php
/cdn-js/wds.min.php
/cdn/zwmrqqgqnaww.php
/cdn/zwewmrqqgqnaww.php
e9580370160d39ef010dfdbfa614820cfe464507ce344a11bcbe760902297c8f
0b28e9df9daf8a3d0aa3dc8a066a34134916dfacd9ba5d25d78e097525f66492
ClearFake:
Chrome lure on:
/lander/chrome/_index.php
37bba90d20e429ce3fd56847e4e7aaf83c62fdd70a7dbdcd35b6f2569d47d533
ab282db6f1fc4b58272cef47522be19d453126b69f0e421da24487f54d611b2f
Emerging Threats Signatures: (All Open Sigs available for free)
“ET MALWARE SocGholish Domain in (DNS Lookup/TLS SNI) (<domain>)”
“ET MALWARE SocGholish CnC Domain in (DNS Lookup/TLS SNI) (<domain>)”
“ET EXPLOIT_KIT RogueRaticate Domain in (DNS Lookup/TLS SNI) (<domain>)”
“ET EXPLOIT_KIT Keitaro Set-Cookie Inbound to RogueRaticate (4cdcb)”
“ET EXPLOIT_KIT Keitaro Set-Cookie Inbound to RogueRaticate (3a7ee)”
“ET EXPLOIT_KIT Keitaro Set-Cookie Inbound to ClearFake (71eb8)”
“ET EXPLOIT_KIT ZPHP Domain in (DNS Lookup/TLS SNI) (<domain>)”
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




