
Security researchers recently discovered a new Microsoft Office zero-day flaw(Follina) exploited in PowerShell remote code execution attacks. The new vulnerability, tracked as CVE-2022-30190, would let hackers execute malicious PowerShell commands through Microsoft Diagnostic Tool (MSDT).
How Follina targets
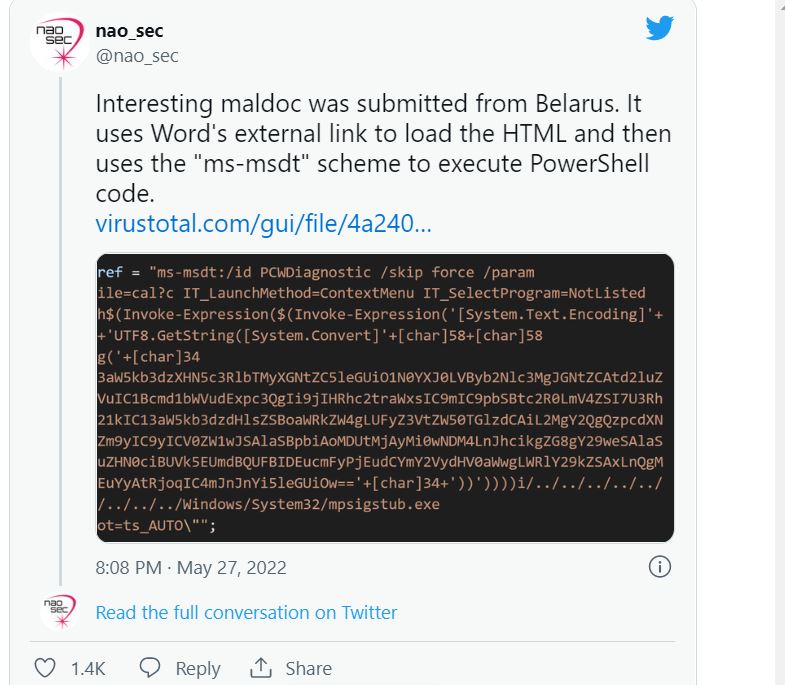
The document uses the Word remote template feature to retrieve a HTML file from a remote webserver, which in turn uses the ms-msdt MSProtocol URI scheme to load some code and execute some PowerShell,” researcher Kevin Beaumont explains “.
The most prominent researchers working on the issue have dubbed the vulnerability in Microsoft Office Follina, because a sample uploaded to VirusTotal included the area code for the Italian comune Follina.
Follina works without elevated privileges, can bypass Windows Defender detection, and doesn’t need macro code enabled to run scripts or execute binaries. The flaw was discovered by accident last Friday when security researcher Nao_sec stumbled upon a malicious Word document submitted to a virus scanning platform.
Affected versions
Researchers have confirmed that exploitation works against Office Pro Plus, Office 2013, Office 2016, Office 2019 and Office 2021.
According to Microsoft’s advisory, the vulnerability affects Windows 7, Windows 8.1, Windows 10, Windows 11, Windows Server 2008, Windows Server 2012, Windows Server 2016, Windows Server 2019, and Windows Server 2022.
Researcher Kevin Beaumont provide an example where an attacker can send an email with this text as a hyperlink:
ms-excel:ofv|u|https://blah.com/poc.xls
And Outlook will allow the user to click the hyperlink and open the Excel document. Because the document isn’t attached to the email, and the URI doesn’t start with http or https, most email gateways are going to let that slide straight through as nothing appears malicious.
Mitigation
There are a few things you can do to stop some or all of the “features” used in this type of attack.
Unregister the ms-msdt protocol
Will Dormann, a vulnerability analyst at the CERT/CC has published a registry fix that will unregister the ms-msdt protocol.
Copy and paste the text into a notepad document:
- Click on File, then Save As…
- Save it to your Desktop, then name the file
disable_ms-msdt.regin the file name box. - Click Save, and close the notepad document.
- Double-click the file
disable_ms-msdt.regon your desktop.
Note, if you are prompted by User Account Control, select Yes or Allow so the fix can continue.
- A message will appear about adding information into the registry, click Yes when prompted
- A prompt should appear that the information was added successfully
Disable preview in Windows Explorer
If you have the preview pane enabled, you can:
- Open File Explorer.
- Click on View Tab.
- Click on Preview Pane to hide it.
Enable Malwarebytes’ Block penetration testing attacks
The Malwarebytes’ Block penetration testing attacks setting is an aggressive detection setting that will block this attack. It is not enabled by default because while enabling it provides additional blocking capabilities for Exploit Protection it can increase false positives, or result in other application conflicts.
To enable it:
- Open Settings
- Click Security
- Choose Advanced settings
- Tick Block penetration testing attacks
File Hash
- f531a7c270d43656e34d578c8e71bc39
- 529c8f3d6d02ba996357aba535f688fc
Microsoft Shares mitigation for Office Zero-day exploit attacks
Fixed Versions
- Microsoft Defender Antivirus Version 1.367.719.0 or newer
Reference
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-30190
Follow us for more, Facebook, Twitter, LinkedIn and Instagram





