
BPFDoor is a traditional backdoor that had been exploited against the Government, telecommunication, Education and Logistics organizations for at least a several years. This was possible because it has been staying under the radar, undetected.
A further analysis in the BPFDoor malware proves that threat actors behind this malware had exploited the old vulnerabilities of the Solaris platform to persist on the targeted systems.
This malware was recently uncovered by the researchers from PwC, during an Incident Response Management in 2021. They track the malware back to the threat actor known as Red Menshen, a China-based group.
WORKING OF MALWARE
The researchers observe that the malware received commands from Virtual Private Servers (VPS) controlled through the compromised routers.
Moreover the researchers from the Sandfly Security showed that the malware is highly evasive and virtually bypass most detection systems.
The BPFDoor – as discussed in a previous article could not be blocked by the firewalls. These malwares can function without opening any ports and not necessarily needs any C2 (Command & Control Server) Server as they can receive commands from any IP Address in the web.
FURTHER RESEARCH
CrowdStrike, a Security Service Provider has observed a threat actor that mainly targets Solaris and Linux Platforms. It also tracks the backdoor with the name “JustForFun” and points the adversary as “DecisiveArchitect”.
BPFDoor is custom-built and implanted in the communication service providers to obtain the sensitive user information.
The research team from CrowdStrike, also exposed in a report today about the details on detecting methods to detect the implant and point the techniques used across the Solaris Platforms.
This “DecisiveArchitect“ achieves perquisite permissions through exploiting one of Solaris system’s vulnerabilities. The CVE-2019-3010 is the vulnerability in the XScreenSaver component of the Solaris platform.
It appears that the threat actor had made the code publicly available for three years and never made any effort to improve it.
The researchers highlight that detecting BPFDoor/JustForFun implants on a Linux system may prove to be a daunting task because the threat actor modifies existing SysVinit scripts on the host to achieve persistence.
To make the malware even more difficult to spot, the file names and paths for the implant and the associated persistence-related scripts are different from one system to another.
INDICATORS OF COMPROMISE
| INDICATOR | PLATFORM | PURPOSE |
| /run/lock/kdumpflush /run/lock/kdumpcab /var/lock/kdumpcab /var/lock/kdumpcache /dev/shm/kdmtmpflush /dev/shm/kdevtmpfls /dev/shm/ff | Linux | JustForFun implant pathnames (temporary – running process) |
| /etc/avahi/avahi.conf /etc/cups/cups /etc/cups/cups.conf /etc/gofer/gofor.conf /etc/gss/gss.conf /etc/jvm/jvm.conf /etc/ntp/ntpd /etc/opt/opt.conf /etc/pm/pm.conf /etc/pulp/agent.conf /etc/ssl/ssl.conf /etc/sysconfig/kdumplog /etc/sysconfig/nfs.conf /etc/sysconfig/pcscd.conf /etc/xdg/xdg.conf /usr/java/jdk1.8.0_181-amd64/.java/init.d/jexecd /usr/local/mysql/bin/myisambug /lib64/libcaac.so.1 | Linux | JustForFun implant pathnames (persistent – on disk) |
| /lib/librbtinfo.so.1 /usr/lib/autofs/mountd /opt/VRTSvcs/bin/IP/online_Agent | Solaris | JustForFun implant pathnames |
| /run/lock/lvv /run/lock/lvm/lv /var/run/lvm/vm /dev/shm/sem | Linux | JustForFun CLI utility pathnames |
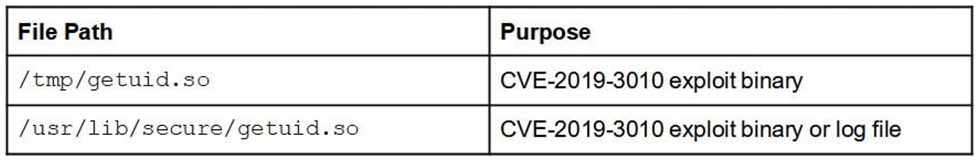
| /tmp/getuid.so /usr/lib/secure/getuid.so | Solaris | CVE-2019-3010 exploitation-related files (not unique to DecisiveArchitect) |
| /usr/local/bin/GetADUsers.py /usr/local/bin/GetNPUsers.py /usr/local/bin/GetUserSPNs.py /usr/local/bin/atexec.py /usr/local/bin/dcomexec.py /usr/local/bin/dpapi.py /usr/local/bin/esentutl.py /usr/local/bin/getArch.py /usr/local/bin/getPac.py /usr/local/bin/getST.py /usr/local/bin/getTGT.py /usr/local/bin/goldenPac.py /usr/local/bin/ifmap.py /usr/local/bin/karmaSMB.py /usr/local/bin/lookupsid.py /usr/local/bin/mimikatz.py /usr/local/bin/mqtt_check.py /usr/local/bin/mssqlclient.py /usr/local/bin/mssqlinstance.py /usr/local/bin/netview.py /usr/local/bin/nmapAnswerMachine.py /usr/local/bin/ntfs-read.py /usr/local/bin/ntlmrelayx.py /usr/local/bin/opdump.py /usr/local/bin/ping.py /usr/local/bin/ping6.py /usr/local/bin/psexec.py /usr/local/bin/raiseChild.py /usr/local/bin/rdp_check.py /usr/local/bin/reg.py /usr/local/bin/registry-read.py /usr/local/bin/rpcdump.py /usr/local/bin/sambaPipe.py /usr/local/bin/samrdump.py /usr/local/bin/secretsdump.py /usr/local/bin/services.py /usr/local/bin/smbclient.py /usr/local/bin/smbexec.py /usr/local/bin/smbrelayx.py /usr/local/bin/smbserver.py /usr/local/bin/sniff.py /usr/local/bin/sniffer.py /usr/local/bin/split.py /usr/local/bin/ticketer.py /usr/local/bin/wmiexec.py /usr/local/bin/wmipersist.py /usr/local/bin/wmiquery.py | Linux | Impacket post-exploitation framework scripts (not unique to DecisiveArchitect) |
| /usr/local/bin/ldapdomaindump /usr/local/bin/ldd2bloodhound | Linux | ldapdomaindump binaries used for Active Directory reconnaissance (not unique to DecisiveArchitect) |
| c:\users\use.bat c:\users\one.ps1 | Windows | Unknown scripts |
SHA-256 Values of Few Sample BPFDoor
96e906128095dead57fdc9ce8688bb889166b67c9a1b8fdb93d7cff7f3836bb9
76bf736b25d5c9aaf6a84edd4e615796fffc338a893b49c120c0b4941ce37925
599ae527f10ddb4625687748b7d3734ee51673b664f2e5d0346e64f85e185683
3a1b174f0c19c28f71e1babde01982c56d38d3672ea14d47c35ae3062e49b155
fd1b20ee5bd429046d3c04e9c675c41e9095bea70e0329bd32d7edd17ebaf68a
5faab159397964e630c4156f8852bcc6ee46df1cdd8be2a8d3f3d8e5980f3bb3
5b2a079690efb5f4e0944353dd883303ffd6bab4aad1f0c88b49a76ddcb28ee9
97a546c7d08ad34dfab74c9c8a96986c54768c592a8dae521ddcf612a84fb8cc
c80bd1c4a796b4d3944a097e96f384c85687daeedcdcf05cc885c8c9b279b09c
c796fc66b655f6107eacbe78a37f0e8a2926f01fecebd9e68a66f0e261f91276
144526d30ae747982079d5d340d1ff116a7963aba2e3ed589e7ebc297ba0c1b3
ac06771774538f33b0e95a92ae1a3e8aaf27e188b51700a03c14ca097af09cac
bd353a28886815f43fe71c561a027fdeff5cd83e17e2055c0e52bea344ae51d3
591198c234416c6ccbcea6967963ca2ca0f17050be7eed1602198308d9127c78






