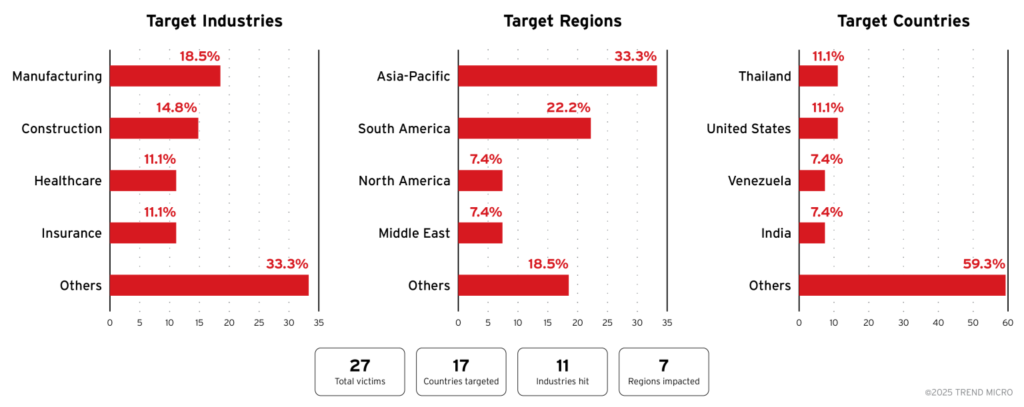
A newly identified ransomware group known as The Gentlemen has been targeting enterprises across 17 countries since August 2025. Advanced evasion techniques are employed by the group to breach manufacturing, construction, healthcare, and insurance sectors. Critical infrastructure risks are heightened, particularly in healthcare, where public safety could be compromised by these ransomware attacks.
Initial access is gained through vulnerabilities in exposed FortiGate servers. Network reconnaissance is conducted using tools like Advanced IP Scanner. Legitimate signed drivers, such as ThrottleBlood.sys, are abused in conjunction with custom executables like All.exe to terminate protected security processes. Customized variants, including Allpatch2.exe, are deployed based on victim environment scans for enhanced defense evasion.
Group Policy Objects (GPO) are manipulated via management console tools and encoded PowerShell scripts to identify domain controllers. Privilege escalation is achieved with PowerRun.exe, while registries are modified to disable authentication controls. Lateral movement is facilitated by PsExec and persistent access is maintained through AnyDesk for command-and-control operations.
Data exfiltration is performed over encrypted channels using WinSCP, with Nmap employed for comprehensive network scanning. Ransomware payloads are deployed via the NETLOGON share, requiring specific password parameters. Backup services, databases, and security processes are aggressively terminated, while forensic artifacts like shadow copies and event logs are deleted to hinder recovery efforts.
The cybersecurity threat posed by The Gentlemen underscores the urgency for robust protections against ransomware exploitation. Internet-facing services must be fortified, and adaptive tactics in enterprise security are essential to mitigate breaches in critical sectors.













Leave A Comment