Cybercriminals are leveraging the flexibility of SVG (Scalable Vector Graphics) files for the dissemination of the GUloader malware.
Hackers Exploit SVG Image Files for GUloader Malware
GuLoader is notorious for its stealth capabilities and capacity to circumvent conventional security measures by employing polymorphic code and encryption.
These features enable it to constantly alter its structure, posing challenges for antivirus software and intrusion detection systems in detecting its presence. SpiderLabs’ observations indicate a significant surge in the utilization of GuLoader.
McAfee Labs has recently detected a campaign involving the distribution of GUloader through malicious SVG files delivered via email.
SVG stands for Scalable Vector Graphics. Furthermore, it is a widely used file format for vector graphics that describes two-dimensional graphics in XML format. Moreover, SVG files are used for various purposes, including web design, icons, logos, illustrations, and interactive graphics.
One of the main advantages of SVG files is that they can be scaled to any size without losing quality, making them ideal for responsive web design and high-resolution displays. Additionally, SVG files can be edited with text editors or graphic design software. Moreover, they support features like animations and interactivity through JavaScript.
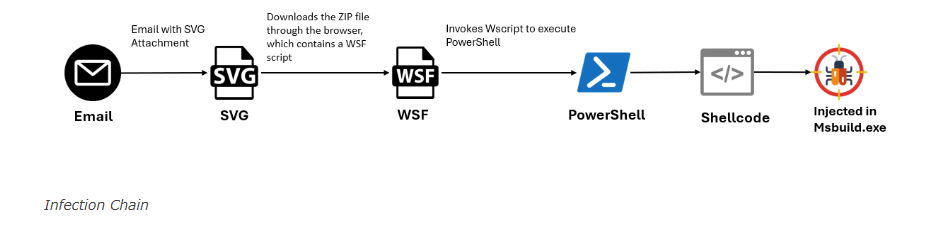
The infection process initiates when a user opens an SVG file attached to an email. This action prompts the browser to download a ZIP file that contains a Windows Script File (WSF).
The WSF file then executes, utilizing wscript to invoke a PowerShell command that establishes a connection to a malicious domain. Consequently, it executes hosted content, including shellcode injected into the MSBuild application.
More details
The attack begins with a spam email containing an SVG file named “dhgle-Skljdf.svg”. Embedded JavaScript within the SVG file triggers the creation of a malicious ZIP archive upon opening.
Once extracted, the ZIP file reveals an obfuscated WSF script, thereby complicating analysis.
This script employs PowerShell to establish a connection to a malicious domain and execute the retrieved content. Additionally, this content includes base64-encoded shellcode and a PowerShell script.
The PowerShell script endeavors to inject the shellcode into the legitimate MSBuild process through the Process Hollowing technique.
Following injection, the shellcode conducts an anti-analysis check and alters the Registry run key to establish persistence.
In the last stage, the process entails downloading and executing the final malicious executable, GUloader, or its variants.
The utilization of SVG files to distribute malware such as GUloader represents a worrisome advancement in the cybersecurity realm.
It’s imperative for organizations and individuals to exercise caution when encountering unexpected email attachments, particularly those containing SVG files.
Additionally, security professionals should prioritize updating their detection systems to effectively mitigate this evolving threat.
IOCs
| File | SHA256/URL |
| 66b04a8aaa06695fd718a7d1baa19386922b58e797634d5ac4ff96e79584f5c1 | |
| SVG | b20ea4faca043274bfbb1f52895c02a15cd0c81a333c40de32ed7ddd2b9b60c0 |
| WSF | 0a196171571adc8eb9edb164b44b7918f83a8425ec3328d9ebbec14d7e9e5d93 |
| URL | hxxps://winderswonders[.]com/JK/Equitably[.]mix |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!












Leave A Comment