A sophisticated Android banking trojan called Herodotus has appeared, using new techniques to evade detection.
All about the malware-Herodotus
Found alongside Hook and Octo during routine monitoring, the samples more closely resemble Brokewell but include original code for advanced evasion. Active campaigns target users in Italy and Brazil, and the malware is being sold as Malware-as-a-Service by a threat actor named K1R0.
ThreatFabric found Herodotus follows modern banking-trojan trends but adds human-like remote-control input to evade behavioral biometric detection.
Herodotus begins with side-loading often delivered through SMiShing links that lure victims to malicious downloads. A custom dropper circumvents Android 13+ Accessibility Service restrictions by auto-installing the payload, opening the Accessibility settings and displaying a convincing loading overlay that hides the prompts used to grant powerful permissions.
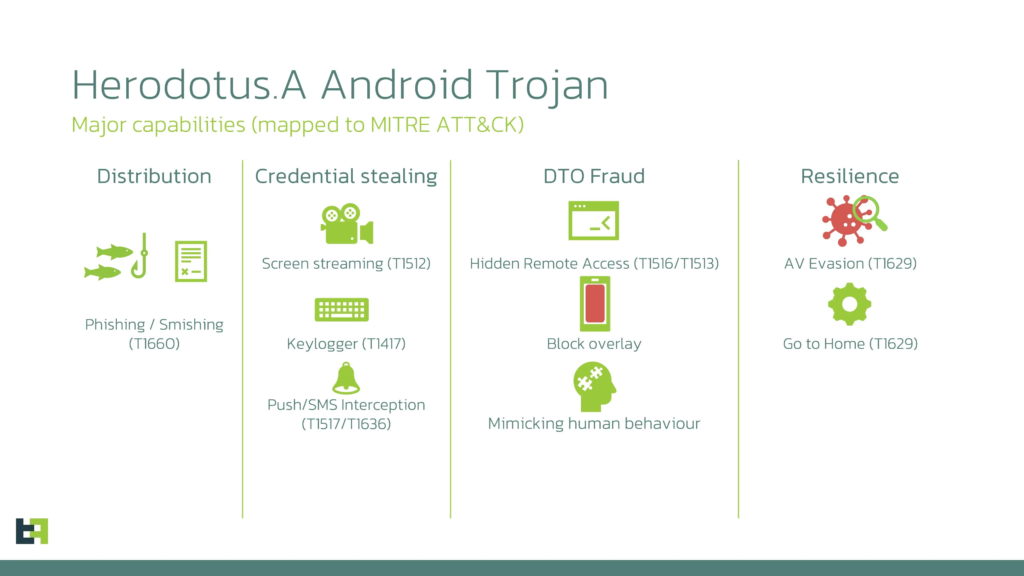
After activation the trojan fingerprints the device by collecting the installed apps and sends that inventory to its command-and-control server, which returns a tailored list of high-value targets and overlay URLs.
The malware then injects realistic-looking fake login screens over legitimate banking apps and intercepts incoming SMS messages so it can harvest credentials and one-time codes in real time.
Where Herodotus stands out is in how it performs input during remote takeover. Instead of pasting whole strings via ACTION_SET_TEXT or the clipboard, which creates instant, machine-like input patterns, it breaks operator-supplied text into single characters and inserts them at randomized intervals.
This per-character, delayed typing produces timing and rhythm very similar to human typing, reducing anomaly signals and making behavioral anti-fraud systems less likely to flag the session as automated.
Herodotus inserts 300–3000 ms delays between keystrokes to mimic human typing and try to fool basic behavioral detectors, though advanced profiling systems can still spot anomalies. Operators enable it with a “Delayed text” checkbox in the control panel.
Indicators of Compromise
Sample
| SHA-256 | Package name | Application name | C2 |
| 53ee40353e17d069b7b7783529edda968ad9ae25a0777f6a644b99551b412083 | com.cd3.app | Chrome | gj23j4jg[.]google-firebase[.]digital |













Leave A Comment