
HTTP Request Smuggling exploits differences in how web servers and intermediaries handle HTTP request sequences. Attackers craft malicious requests to manipulate the processing order, potentially leading to unauthorized access, security bypasses, session hijacking, or injection of malicious content into responses for other users.
This flaw arises from differences in interpreting HTTP request start and end points, causing servers to process them incorrectly.
Cybersecurity researchers at BugCrowd recently unveiled key insights about HTTP Request Smuggling through a collaborative effort by Paolo Arnolfo (@sw33tLie), an enthusiast of server-side vulnerabilities, Guillermo Gregorio (@bsysop), a skilled hacker, and █████ (@medusa_1), a stealthy genius.
New TE.0 HTTP Request Smuggling
While cloud hosting offers security benefits, unknown HTTP Request Smuggling vectors can still pose significant threats. A recent discovery revealed vulnerabilities in thousands of Google Cloud-hosted websites using their Load Balancer, compromising various services, including Identity-Aware Proxy.
Researchers use differential testing tools like http-garden for local servers and “spray-and-pray” techniques on bug bounty programs for cloud infrastructures to uncover such vulnerabilities. Tools like bbscope can generate extensive target lists for vulnerability research, underscoring that HTTP Request Smuggling remains a widespread and under-researched security issue.
TE.0, a new HTTP request smuggling variant, was discovered affecting Google Cloud’s Load Balancer.
The TE.0 HTTP Request Smuggling vulnerability affected numerous targets, including those protected by Google’s Identity-Aware Proxy (IAP), and was prevalent among Google Cloud-hosted websites using HTTP/1.1 by default.
This flaw compromised Google’s Load Balancer and IAP, bypassing strict authentication and authorization measures, leading to potential security breaches. This discovery underscores the evolving nature of HTTP Request Smuggling and the necessity for ongoing security research in cloud infrastructures.
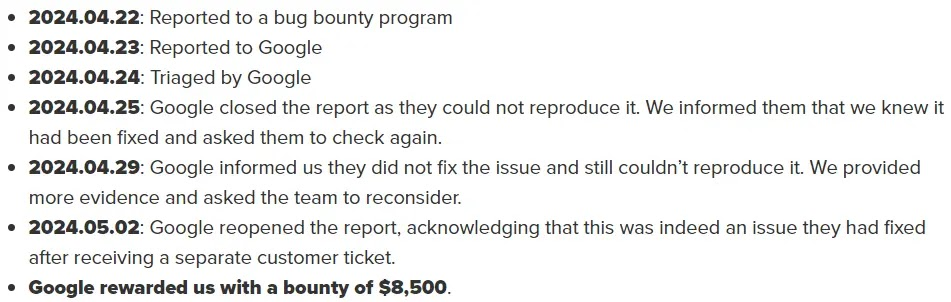
Google acknowledged the issue after initial reporting challenges, highlighting the complexity of addressing loopholes in cloud infrastructure.
Disclosure timeline:
Google Cloud’s infrastructure was found to have a significant vulnerability due to persistent HTTP request smuggling attacks.
Research driven by curiosity led to a substantial reward and underscored the importance of creative thinking in cybersecurity.






