Black Basta, a new ransomware has started its play during the month of April, with a start of approximately ten to fifteen companies.
The first KNOWN attack of this group was in the second week of this April month and started its expansion through the world.
As the name ‘ransomware’ implies, the group demands for a ransom from the victims of their attack. This ransom is demanded for the sake of the privacy of the data currently encrypted by the group and its decryption key.
The Black Basta is still buried beneath the surface, so nothing more is known about this group. But their quick spread and negotiation style is making it dubious. Whether this “BLACK BASTA” is a new group or just a rebrand of an existing on-the-top ransomware group.
Applied Strategy
Using the double-extortion strategy, Black Basta will exfiltrate the data and documents before encrypting the organizations’ devices. With this exfiltrated data, they demand the organization to pay a ransom in exchange for the decryption key and the privacy of the stolen data.
The attack is continued on the TOR site – ‘Black Basta Blog’ (or) ‘Basta news’, which contains the list of all the victims who have not paid the ransom. Black Basta enforces them more by deliberately releasing the data of the victims.

Black Basta – An Interpretation
An analysis made by the BleepingComputer with the help of a few online samples shows that when executed, the Black Basta encryptor needs the administrative privileges to run and encrypt the files. Once it is launched, the encryptor will delete the Volume Shadow Copies with the following command,
C:\Windows\system32\cmd.exe /c
C:\Windows\SysNative\vssadmin.exe delete shadows /all /quiet
After the Volume Shadow Copies are deleted, it will hijack an existing Windows service and uses that service to launch the ransomware executable file. In the test conducted by BleepingComputer, the FAX service was hijacked. As in the following image,

The wallpaper is also changed by the ransomware to display a message to the victim as shown below,

How does it works from the inside?
The ransomware will now reboot the system into “Safe Mode with Networking”, where the hijacked Windows service (In this case, a Fax) will start and automatically begin to encrypt the files on the device.
Ransomware expert Michael Gillespie, who analyzed Black Basta’s encryption process, says that it utilizes the ChaCha20 algorithm to encrypt files. The ChaCha20 encryption key is then encrypted with a public RSA-4096 key included in the executable.
While encrypting files, the ransomware will append the .basta extension to the encrypted file’s name. So, for example, ‘test.jpg‘ would be encrypted and renamed to ‘test.jpg.basta’.

For the custom icon to display with the .basta extension, the ransomware will create a custom extension in the Windows Registry and associate the icon with a randomly named ICO file in the %Temp% folder.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.basta]
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.basta\DefaultIcon]
@="C:\\Windows\\TEMP\\fkdjsadasd.ico"
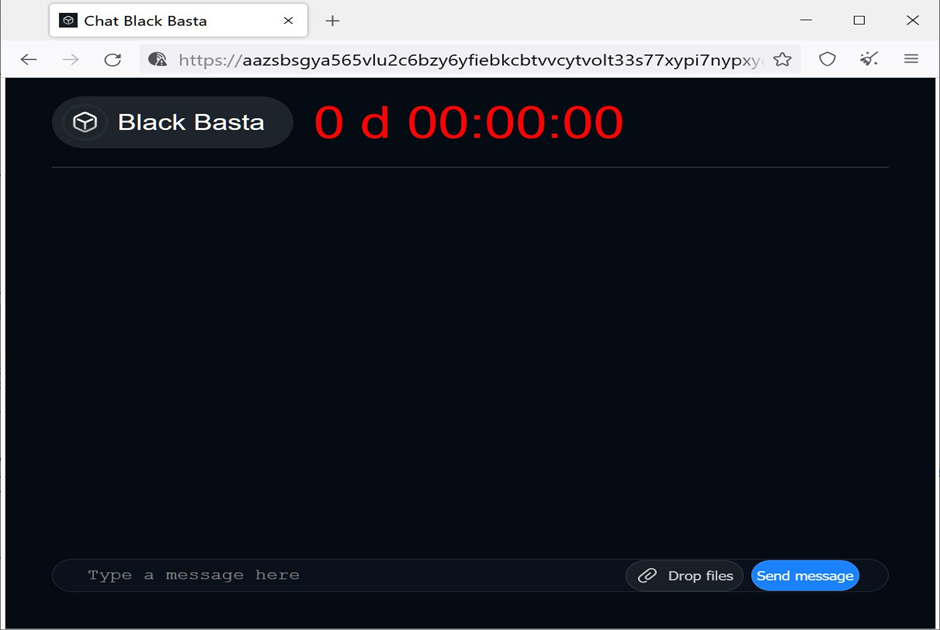
In each folder on the encrypted device, the ransomware will create a readme.txt file that contains information about the attack and a link and unique ID required to log in to their negotiation chat session.

The TOR negotiation site is titled ‘Chat Black Basta‘ and only includes a login screen and a web chat that is used for negotiation with the threat actors.
The threat actors use this screen to issue a threat that privacy of the data will be compromised if payment is not made in seven days, and the promise of a security report after a ransom is paid.
Unfortunately, Gillespie says that the encryption algorithm is secure and that there is no way to recover files for free.
Theories
The one theory discussed between “MalwareHunterTeam” and the author of BleepingComputer is that Black Basta is possibly an upcoming rebrand of the Conti ransomware operation.
Conti has been under heavy scrutiny over the past two months after an Ukrainian researcher exposed their private conversations and the ransomware’s source code.
Due to this, it has been conjectured that Conti would rebrand their operation to evade law enforcement and to start over under a different name.
A few hunting team are sure that this ransomware is under development phase and this group had claimed that they were the “no-name-software“.
Recommendations
- Ensure backup policy is live.
- Enable constant monitoring over the file extensions and custom icons through out your organizational environment.
- It is crucial to have a reputable anti-virus installed and kept updated.
- Avoid opening suspicious mail contents.







