
A significant cybersecurity breach has compromised the privacy of users accessing one of the internet’s most infamous illegal marketplaces.
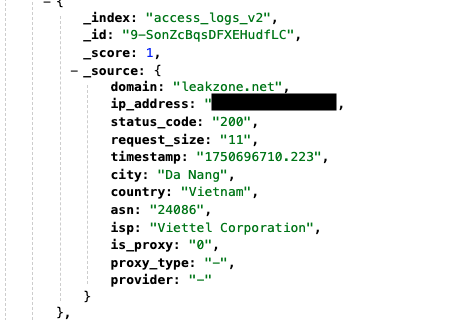
On Friday, July 18, cybersecurity firm UpGuard uncovered an unsecured Elasticsearch database containing around 22 million records of web requests. Notably, 95% of the traffic was linked to leakzone[.]net, a well-known “leaking and cracking forum” that enables the sharing of hacking tools, exploits, and stolen accounts.
Each entry in the exposed database contained crucial user information, such as IP addresses, geographic locations, and internet service provider details. This data effectively created a detailed map of visitor activity on the underground cybercrime platform.
Exposes 22 Million Leakzone Records
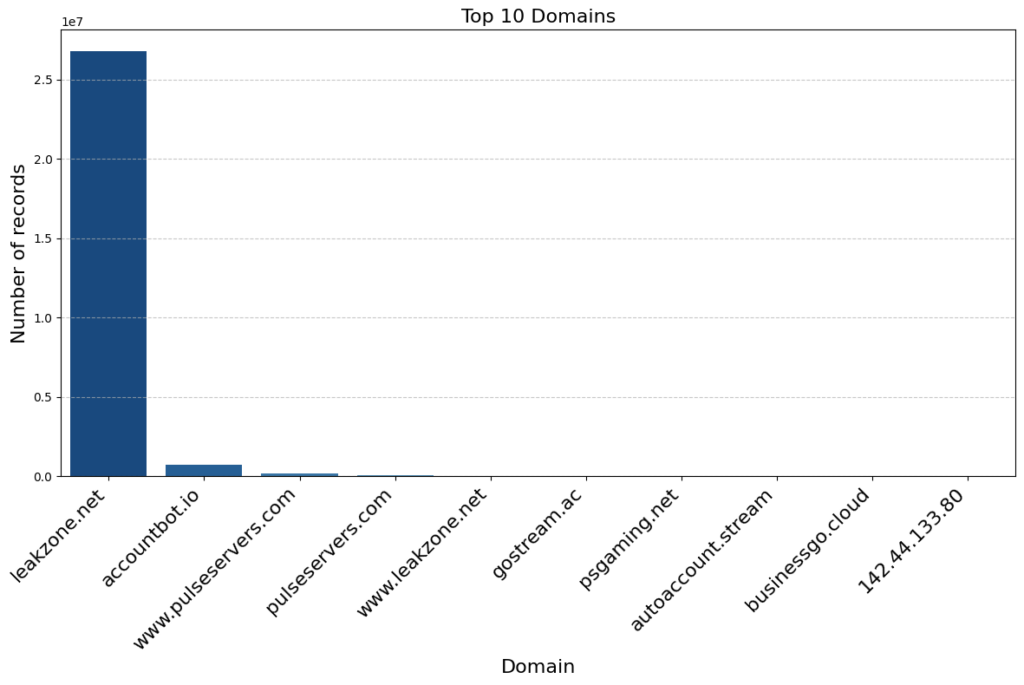
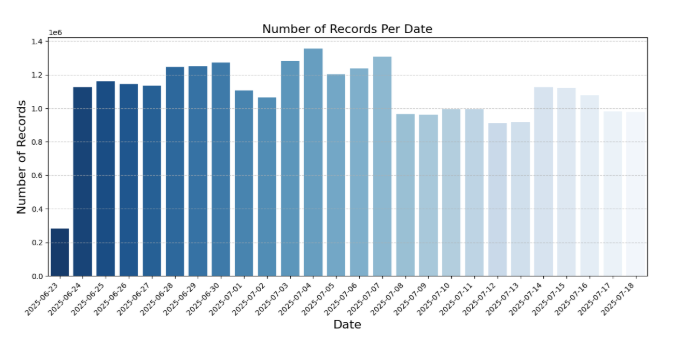
The exposed Elasticsearch database held records dating from June 25 up until its discovery, logging around one million requests per day. The median size of each request was approximately 2,862 bytes.
The database schema revealed that 185,000 unique IP addresses accessed the platform over the three-week period, far surpassing Leakzone’s registered user base of 109,000 accounts, as reported by UpGuard.
The discrepancy between the number of unique IP addresses and registered user accounts suggests that users employed advanced privacy measures, such as dynamic IP addresses and proxy servers, to mask their identities.
Further technical analysis revealed that approximately 5% of the requests (1,375,599 total records from 3,983 IP addresses) were routed through public proxies, identified by database fields marked “is_proxy” and “proxy_type” with the label “PUB.”
More notably, investigators found extensive evidence of VPN usage, particularly through infrastructure linked to Cogent Communications. The third, fourth, and sixth most active IP addresses were all tied to this VPN service provider, indicating that these IPs were likely VPN exit nodes serving multiple users rather than individual connections.
The exposure of this data carries serious privacy risks for users of the illicit forum, as IP addresses are considered Personally Identifiable Information (PII) under GDPR regulations due to their ability to track users across platforms.
Geographic analysis of the traffic revealed a global distribution, with one interesting anomaly: there were no direct connections from China. This suggests that users from China are likely routing their traffic through proxy servers located in other countries to avoid detection.
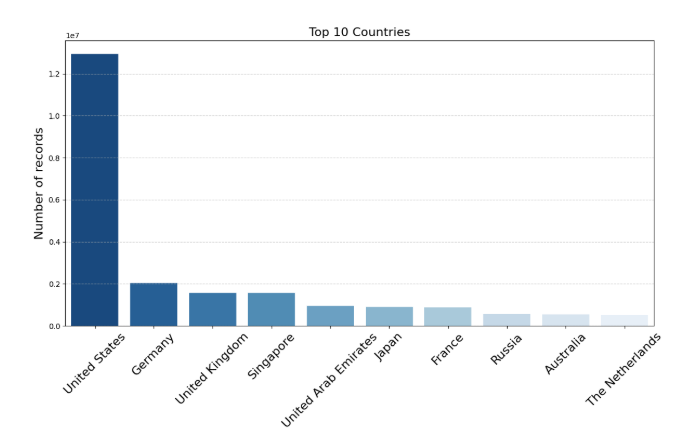
Cloud service providers like Amazon, Microsoft, and Google were notably present in the traffic logs, suggesting that users are relying on mainstream infrastructure for anonymization. This highlights how even high-profile, reputable services are being used by individuals attempting to hide their identity while engaging in illicit activities.
The breach underscores a significant vulnerability for users who believe they can remain anonymous on illegal platforms. While 39% of the IP addresses appeared only once in the logs, possibly indicating users without VPN protection, the heavy concentration of traffic through identifiable VPN services opens up new avenues for surveillance.
This trend is especially concerning in light of recent law enforcement successes, such as the arrest of the suspected administrator of the XSS[.]is Russian hacking forum, showing that even those using sophisticated anonymization tactics are not beyond the reach of authorities.








Some lady contacted me on IG and got me to trade with this company. Constantly convincing me for one reason to the other to keep increasing my deposits. Long story short, I lost about $88,000 I’ve never been so disappointed in my life, trusted them only to be deceived like this. Just another one of those shady companies that have nothing to offer. Wish I had read some comments in forums earlier, wouldn’t have dealt with them. Glad I found a reliable expert at Henry Walter in some forums who helped me get back everything I lost. If you’re also a victim of these guys or lost your money to similar companies, write me and I’ll refer you to the Recovery Experts. I’ll make sure you get back everything you lost Email: davidmoore9951 (@) GM AIL , C0M