
Emotet (also known as SpmTools) is a sophisticated, modular banking trojan. Emotetmostly serves as a downloader or dropper of other banking trojans. It is a loader-as-a-service (LaaS). It is mainly distributed by spam emails (malspam).
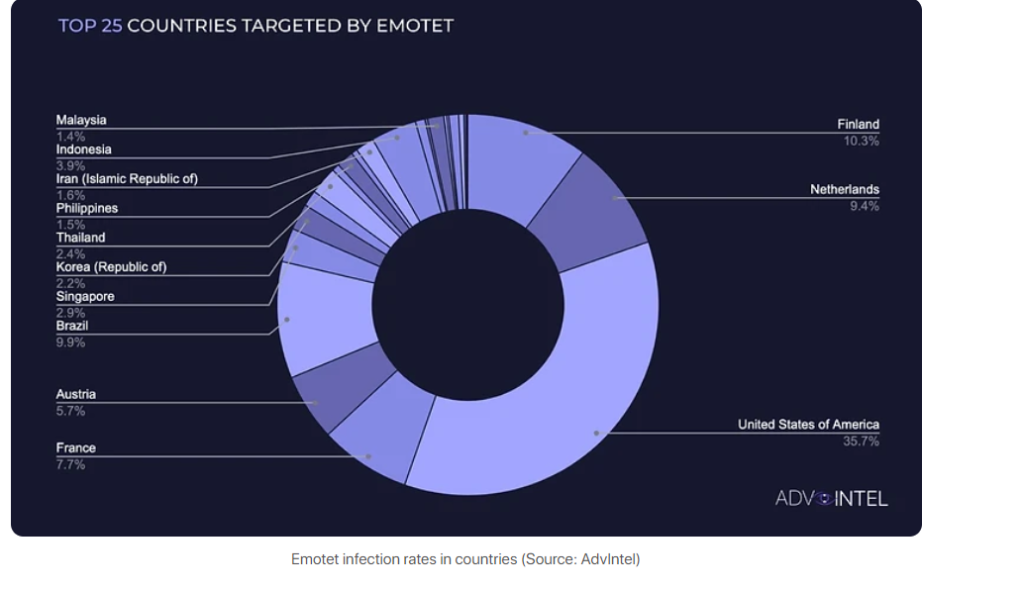
AdvIntel recorded 1,267,598total Emotet infections globally in 2022. Further data from the research shows that Emotet infections peaked at the beginning of the Russian/Ukrainian crisis, with groups like Quantum and BlackCat starting to use the malware after conti. The malware’s most targeted country is the U.S., with an approximately 36% rate.
From November 2021 to Conti’s dissolution in June 2022, Emotet was an exclusive Conti ransomware tool, however, the Emotet infection chain is currently attributed to Quantum and BlackCat.
Emotet’s botnet attack flow utilizes Cobalt Strike to launch ransomware. In other words, threat actors presently use Emotet primarily as a dropper or downloader for a Cobalt Strike beacon, which distributes a payload enabling threat actors to hijack networks and carry out ransomware operations.
Loader Malware Emotet’s IOCS
- https://xsnonline.us/blogs/4x466v/
- http://jimlowry.com/9tag/
- https://saeblaser.com/wp-admin/jx7w814/
- https://kulshai.com/wp-includes/7fslng/
- https://progea4d.pl/waloryzacja-przyrodnicza-kamieniolomow-mydlniki-oraz-bodzow/
- https://www.altinoluk-akcay.com/9uZYqjHN/
- https://fractal.vn/users_contact/ol-e-g-d-m-i-tr-ie-nko4-9-7gmail-com/
Emotet botnet IoCs can be found here. CIRT published a longer list of IoCs.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!





