
Cybersecurity and secure nerwork concept. Data protection, gdrp. Glowing futuristic backround with lock on digital integrated circuit.
Recent research uncovered websites deploying Lumma Stealer disguised as browser updates. These sites, posing as tutorial pages with legitimate-looking guides, open a malicious JS iframe using the ClearFake framework. Some have been active for weeks.
LUMMA STEALER
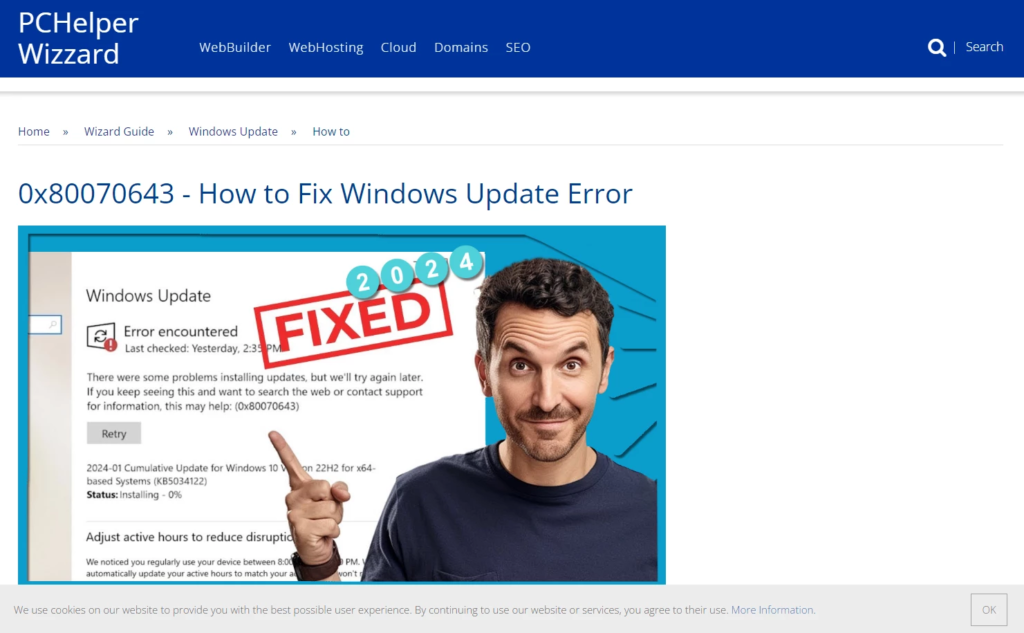
A new Lumma Stealer campaign has emerged on fake tutorial sites. Avast reports one such site, pchelperspro[.]com, which uses the ClearFake JS framework to trick users into running a payload. The site appears to offer instructions on solving Windows update issues, but attentive users may notice all buttons are inactive and sourced from a different site.
After a short delay, the ClearFake framework triggers a fake browser update window. Its design and functionality make it seem legitimate unless you know that web browsers never display such windows. Following the fake update prompts leads users to download and run a malicious PowerShell script.
The PowerShell script connects to a command server, loads, and executes the final payload, Lumma Stealer. Additionally, the script performs system fingerprinting with the following queries:
The script encodes command server addresses to resemble sketchy online shops. However, each was created only 20 days ago, which is unlikely to be a coincidence:
- Standingcomperewhitwo.shop
- Innerverdanytiresw.shop
- Lamentablegapingkwaq.shop
- Sturdyregularrmsnhw.shop
- Stickyyummyskiwffe.shop
- Greentastellesqwm.shop
ClearFake is a JavaScript framework that creates JS iframes with any content, bypassing browser protections. First spotted in August 2023, it has been widely used in similar attack campaigns. Like the current campaign, it displayed “update your browser” pages customized by browser. The main difference now is the use of fake websites instead of compromised ones.
Lumma Stealer, a well-known malware, appeared in early 2023 and quickly gained popularity on the Darknet. Designed for minimal footprint, it evades detection by traditional antivirus software. Its flexible distribution methods, such as YouTube promos for cracked software and Discord spam, have fueled its rise. Functionally, Lumma is a modular infostealer that collects passwords, session tokens, cryptowallet data, and more.
Recommendation
With GridinSoft Anti-Malware, you can avoid shady sites and malicious frameworks before they cause harm. Its network security module analyzes activities using multiple detection systems. Continuous database updates ensure peak efficiency against the latest threats. Try it now!




