
Hackers exploit malicious Python packages to attack developer environments, inject harmful code, and steal sensitive information or install malware. This method leverages popular repositories for broad impact with minimal effort.
CheckMarx researchers recently found that attackers are using the malicious package “lr-utils-lib” to target macOS developers and steal Google Cloud logins.
Malicious Python Package Targets macOS Developers
A malicious package named “lr-utils-lib” targets macOS systems to steal Google Cloud Platform credentials. Its setup.py file includes hidden code that activates upon installation, specifically targeting macOS by checking the system type and comparing the IOPlatformUUID with 64 known hashes.
When a match is found, the malware extracts sensitive data from ~/.config/gcloud/application_default_credentials.json and credentials.db files, then sends this information to a remote server (europe-west2-workload-422915.cloudfunctions.net).

The “lr-utils-lib” malware attack involved a fake LinkedIn profile under “Lucid Zenith,” falsely claiming to be the CEO of Apex Companies, LLC. This incident highlights the sophistication of modern cyber threats, combining malware distribution, social engineering, and AI verification flaws.
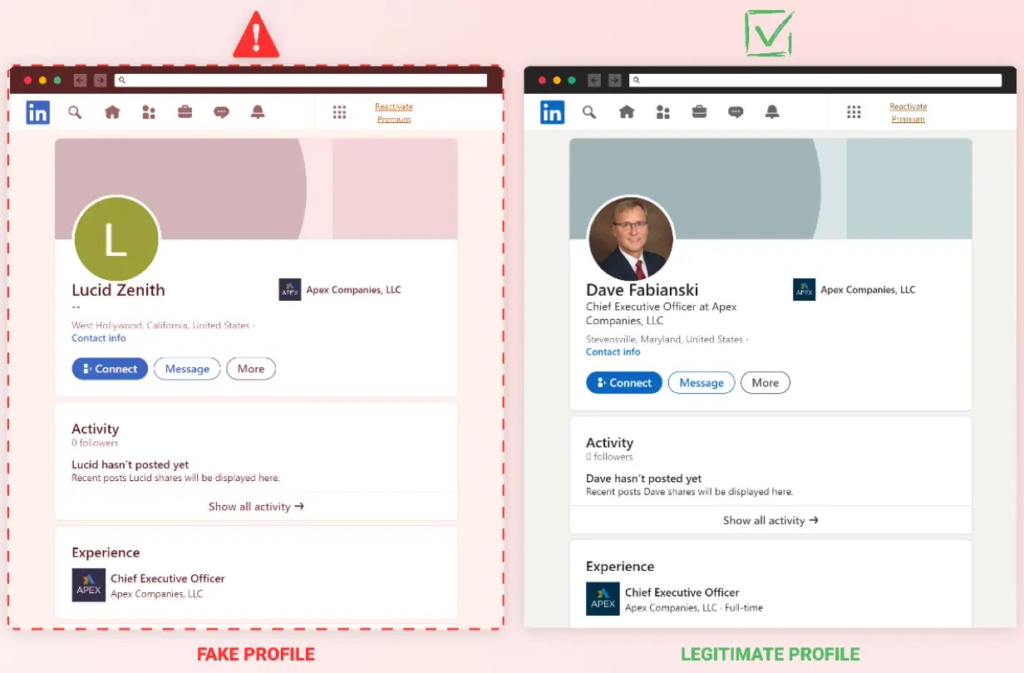
AI-driven search engines failed to properly verify the fake LinkedIn profile, which shows how threat actors exploit flaws in AI verification. This highlights the need for thorough checks and multiple sources when using AI tools.
The “lr-utils-lib” package attacks macOS users to steal Google Cloud credentials, emphasizing the importance of securing third-party packages.
This case underscores broader cybersecurity issues, such as the impact of fake profiles and unreliable AI verifiers. It demonstrates the need for rigorous vetting and careful information-seeking to prevent data breaches and reputational damage.
IOCs
- europe-west2-workload-422915[.]cloudfunctions[.]net
- lucid[.]zeniths[.]0j@icloud[.]com
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




