
With no official streaming release for the new Snow White, many users are resorting to piracy, making them vulnerable to cyber threats. Veriti researchers uncovered a campaign where attackers distribute malware through torrent sites, exploiting eager viewers looking for unauthorized downloads.
Malicious Snow White downloads
The post was malicious, redirecting users to a torrent with an infected file. Attackers likely gained access through an XSS vulnerability or leaked admin credentials.
The blog post redirected users to a torrent with three files, including a malicious executable disguised as a codec installer.
Veriti analysts found a suspicious file named xmph_codec.exe in the torrent, disguised as a required video codec.
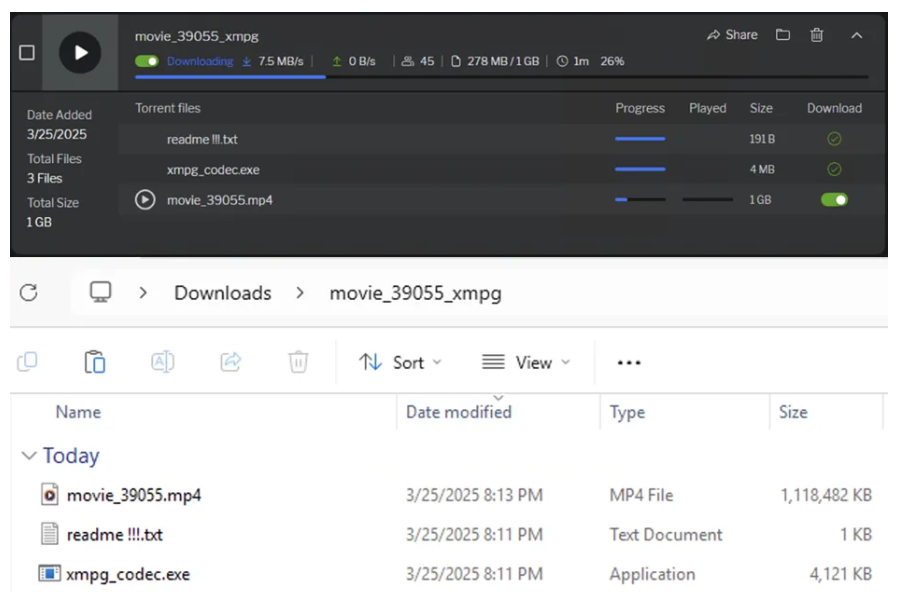
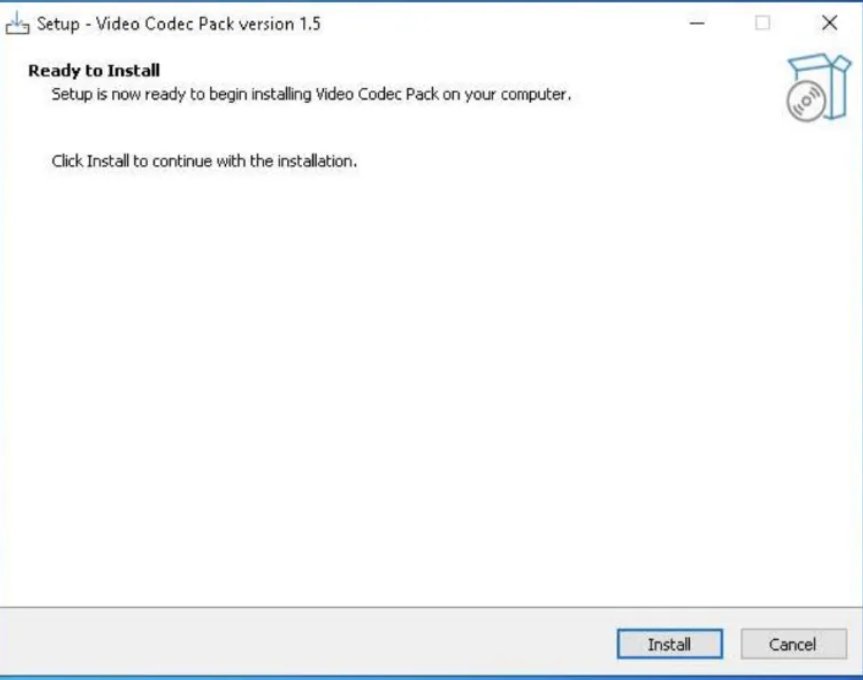
When executed, the file triggered a complex malware deployment process. Key findings include:
- Detection: 50 out of 73 security vendors on VirusTotal flagged it as malicious.
- Compilation: Compiled on July 12, 2024, suggesting reuse from previous campaigns.
- Unsigned Executable: Indicates suspicious origins.
- Malicious Actions: Drops additional malware, installs the TOR browser, connects to a Dark Web .onion domain, and disables security features like Windows Defender.
The malware communicates with a C2 server on the Onion network:
http[:]//cgky6bn6ux5wvlybtmm3z255igt52ljml2ngnc5qp3cnw5jlglamisad.onionhttp[:]//cgky6bn6ux5wvlybtmm3z255igt52ljml2ngnc5qp3cnw5jlglamisad.onion/route.php
This campaign uses the anonymity of the TOR network to avoid detection. With the lack of digital streaming options for major movies like Snow White, users are being pushed towards illegal downloads, creating an opportunity for attackers.
To protect against such malware, users should stick to reputable streaming platforms, supporting legal content creators while ensuring device security. Stay informed on evolving cybersecurity tactics to protect your digital safety.
IOCs
File hashes:
- 9c1a0608bae991af50096acaec9d979df9f9a3bb6e89d9d20972d6cfeb9582bb
- 2ec555c34f0af1514501ca5e4d999c843d5b9de7973467820fcf6034a517c4cc
- 8b81b0017c0e154c1fdea226f1ad0d3cfc0e301af05698bdbb7d0d6037d71a12
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




