
Hackers used Microsoft Teams to trick victims into granting remote system access, showcasing advanced social engineering tactics, according to Trend Micro.
All about the attack – Microsoft Teams Exploit
The attack began with a flood of phishing emails targeting the victim. Shortly after, the attacker initiated a Microsoft Teams call, posing as an employee of a trusted client.
During the call, the attacker instructed the victim to download a remote support application, initially proposing Microsoft Remote Support. When installation from the Microsoft Store failed, the attacker pivoted to AnyDesk, a legitimate remote desktop tool often exploited by cybercriminals.
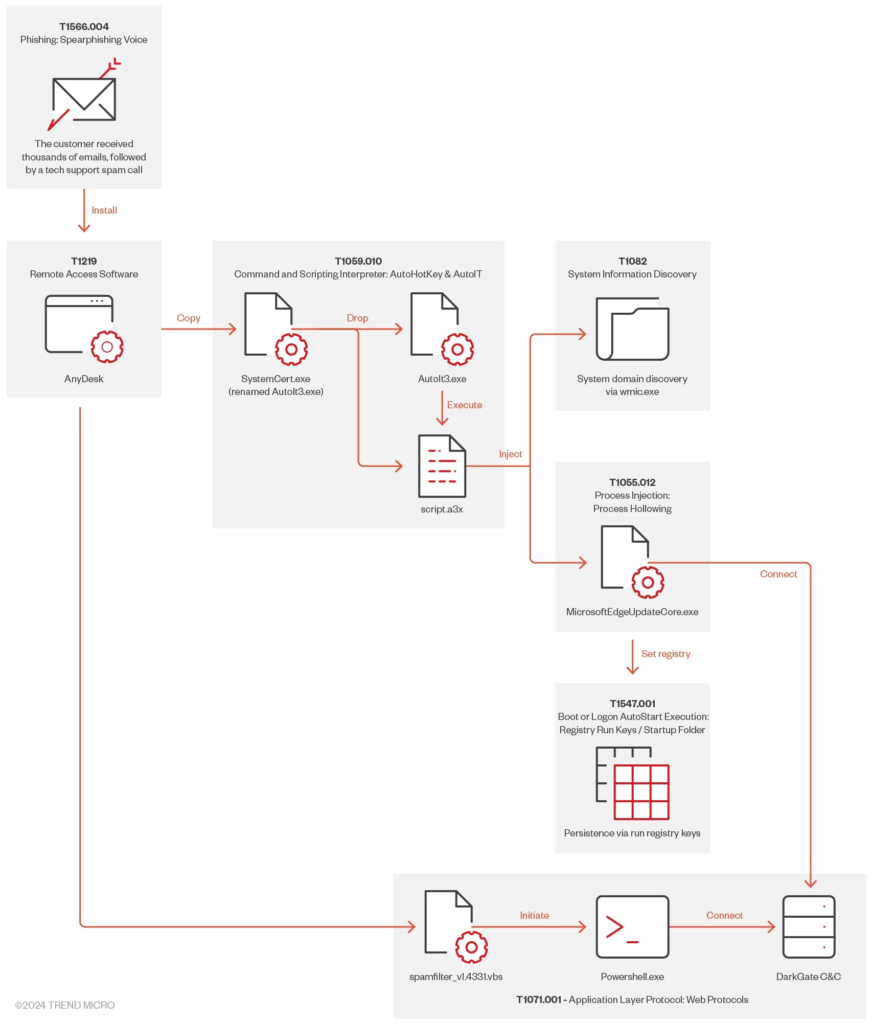
After installing AnyDesk, the attacker took control of the victim’s system, deploying suspicious files, including the Trojan.AutoIt.DARKGATE.D. This malware, delivered via an AutoIt script, enabled remote control, malicious commands, and C2 server connections.
After gaining access through AnyDesk, the attacker executed commands like systeminfo, route print, and ipconfig /all to collect detailed information about the system’s hardware, software, and network setup. The data was saved in a file named 123.txt for further reconnaissance.
The malware also employed evasion techniques, using AutoIt scripts to detect antivirus software and bypass defenses. Additionally, it downloaded and extracted malicious files into hidden directories to maintain persistence and avoid detection.
A malicious file, SystemCert.exe, created scripts and executables in temporary folders, enabling connections to a C2 server and downloading more payloads. Fortunately, the attack was stopped before any data was stolen. While persistent files and registry entries were created, no sensitive information was compromised.
This incident highlights the importance of strong security practices:
- Verify Third-Party Claims: Confirm the legitimacy of third-party support providers before granting access.
- Control Remote Access Tools: Use approved tools like AnyDesk and enforce MFA for added protection.
- Employee Training: Educate staff on phishing and vishing to reduce risks.
The attack demonstrates how cybercriminals exploit trust and platforms like Microsoft Teams, stressing the need for vigilance and robust defenses.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




