
Microsoft warns that cybercriminals are using Cobalt Strike to infect entire networks beyond the infection point, according to a report.
Ads On Microsoft Teams Update:
Attackers are using fake Microsoft Teams updates to deploy backdoors, which use Cobalt Strike to infect companies’ networks with malware.
Certainly, the Cobalt Strike attack is a paid penetration testing product that allows an attacker to deploy an agent named ‘Beacon’ on the victim machine.
Firstly, these attacks targets organization’s to compromise the rest of the network. But recent ones focuses on the education sector, which depends on Videoconferencing due to the COVID-19 situation.
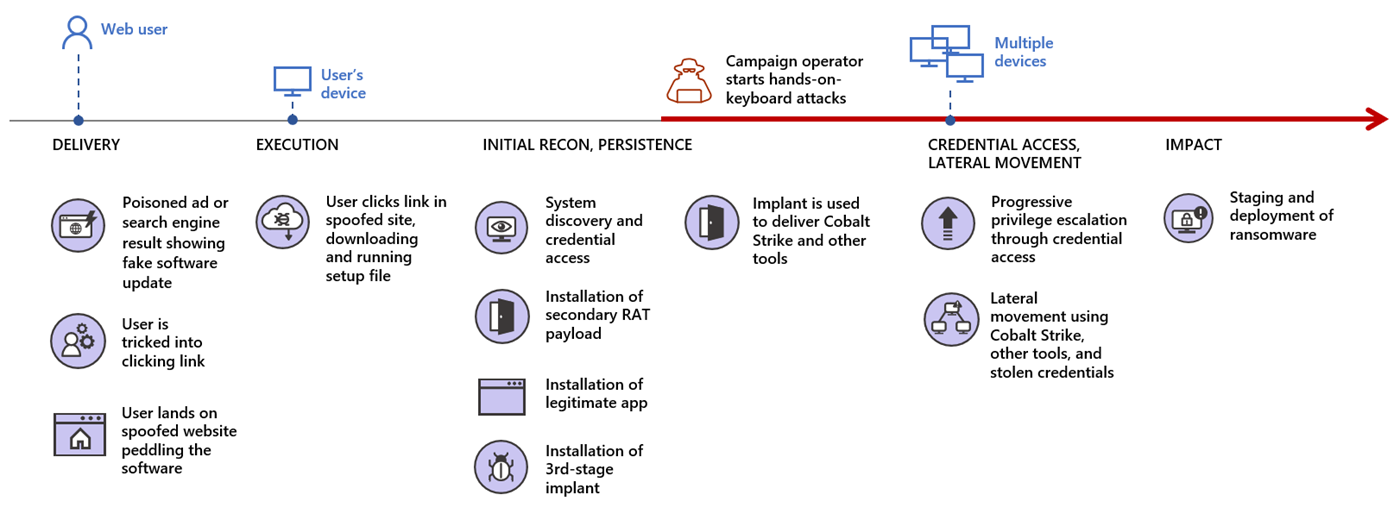
Attackers in the latest FakeUpdates campaign using search-engine ads to push top results for Teams software to a domain that they control and use for nefarious activity, Microsoft advisory report
If victims click on the link, it downloads a payload that executes a PowerShell script, which loads malicious content.
Recently, threat actors were seen using Cobalt Strike in attacks exploiting Zerologon, a privilege-elevation flaw that allows attackers to access a domain controller and completely compromise all Active Directory identity services.
Follow Us on Twitter, LinkedIn To Get Latest Security News
Subscribe – FirstHackers News
Mitigation Steps For The Latest Wave of FakeUpdates:
- Ensure local admin passwords are strong and to use web browsers that can filter and block malicious websites.
- Admin privileges also should be limited and avoid domain-wide service accounts that have the same permissions as an administrator.
- Microsoft recommended organizations to block executable files, blocking JavaScript and VBScript code from downloading executable content.







