Due to the hiking interests towards the Pixelmon NFT Site, the threat actors have turned their attention towards them.
Pixelmon is an Open World RPG NFT game. The player can collect, train, and battle other players using Pixelmon pets in the Metaverse.
Threat actors have basically replicated the Pixelmon(.)club (Pixelmon official website) as Pixelmon(.)pw to allure the victims.
MALWARE BEHAVIOR
The phony website hoaxes the demo of the project’s game with a .exe file that installs the password-stealing malware. The Installer.zip is the .exe file, which looks like a corrupted file rather a malware infecting one.
The MalwareHunterTeam, has found other malicious files distributed by the site which led to the discovery of the spreading malware.

Setup.zip, one of the files distributed by the phony site, contains the Setup.ink file. This “Setup.ink” file is a windows shortcut that executes a Powershell command to download a system32.hta file from Pixelmon(.)pw.
While testing these malicious payloads, BleepingComputer observed that the system32.hta file downloaded Vidar – a password-stealing malware, that too a formerly used one.
During the execution, the malware retrieves the IP Address of C2 Server after connecting to a telegram channel. Then the malware, retrieves the configuration command from the C2 server and download more modules for the purpose of stealing the data from the compromised device.
The Vidar malware steals passwords from different sources such as browsers and applications and even search the device for files that matches the stolen data and uploads them to the threat actor.
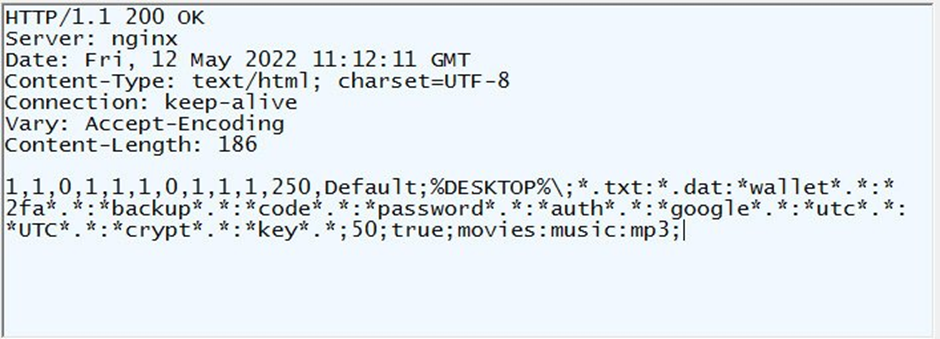
As shown above in the malware configuration, the C2 server instructs the malware to search and steal the files including the text files, binary files, crypto wallet information, authentication files, backup files, codes, passwords, test cases and more.
The threat actor expects the victim to have a crypto wallet because the phony site is an NFT website. Thus, the search for the crypto currencies would be intensified.
BleepingComputer remarks that the threat actors are repeatedly changing the site over the past few days and the payloads available previously are not in sight presently.
RECOMMENDATIONS
With the overwhelming activity on the site, the researchers expect the campaign to remain active and possibly for adding working threats.
Reckoning the raise in threat actors exploiting the NFT projects for robbing you crypto-wallets and not leave a penny. The Crypto investors are advised to check on the URL of the website before planning further. In addition, be cautious about executing the executable files from unknown websites by scanning them with anti-virus software.







