
Cybersecurity researchers have discovered a new campaign attributed to the chinese “Tropic Trooper” hacking group. Tropic Trooper was previously observed targeting Philippines, Hong Kong and Taiwan; while the two latest are Chinese-speaking countries. This employs a novel loader called Nimbda and a new variant of the Yahoyah trojan.
The trojan is bundled in a greyware tool named ‘SMS Bomber,’ which is used for denial of service (DoS) attacks against phones, flooding them with messages. Tools like this are commonly used by “beginner” threat actors who want to launch attacks against sites.
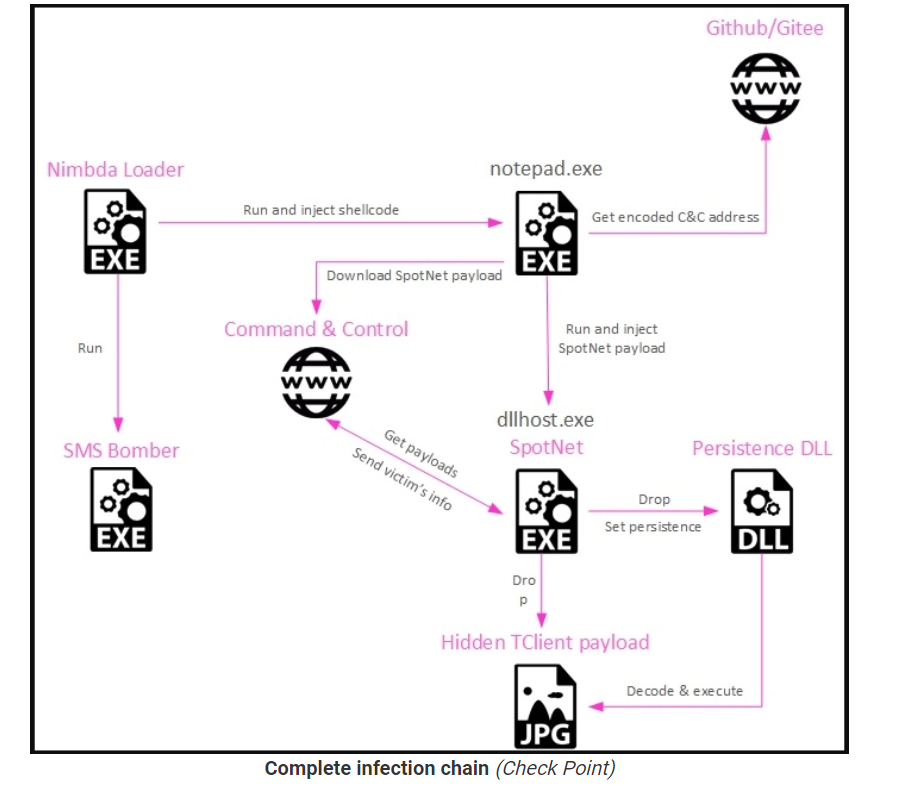
Nimbda contains an embedded executable, an SMS Bomber, which it drops into the victim’s temp folder and then executes. Following that, Nimbda separately injects a different piece of code into a launched notepad.exe process.
This payload is the new Yahoyah variant collects information about local wireless network SSIDs in the victim machine’s vicinity.The collected information is formatted and sent to the C&C server.
The final payload, dropped by the Yahoyah executable, is encoded in a JPG image using steganography. Check Point identifies it as ‘TClient,’ a backdoor Tropic Trooper used in past campaigns.
While the exact targeting scope is unknown, this campaign demonstrates Tropic Trooper’s capability to create any decoy needed for their operations, cryptographic knowledge, and malware development activity.
File Hash
- 8ee94c4d4e13bf59524e1d3eb9c8c846
- 916e8b1a9d91f3649b33dd8bc0f09a8d
- 68a3198fd77a063f46a1d3cddb266f02




