The ongoing Middle East conflict has significantly elevated cyber risk across the region. During periods of geopolitical...
A new scam is targeting Zoom users by exploiting trust in meeting invitations. In just twelve days,...
A hacker reportedly manipulated Anthropic’s Claude AI to assist in a coordinated cyberattack against Mexican government agencies,...
Microsoft says attackers are creating fake Next.js projects to trick developers. These projects look normal and often...
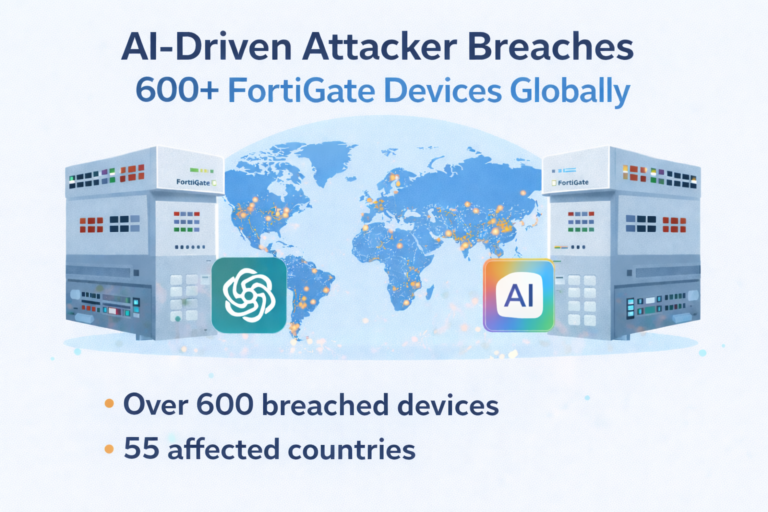
A financially motivated threat actor used commercial generative AI tools to compromise more than 600 FortiGate devices...