Passwordstate app’s update hijacked to install malware in a supply-chain attack after breaching its networks.
Supply Chain Attack — Passwordstate
Passwordstate password management app notified users on a supply chain attack and recommended to reset their passwords.
Supply chain attack — cyber-attack that seeks to damage an organization by targeting less-secure elements in the supply chain.
Click Studios, the company behind the Passwordstate enterprise password manager, said the malicious update exposed Passwordstate customers.
In addition, over 370,000 security and IT professionals at 29,000 companies are using the password manager worldwide.
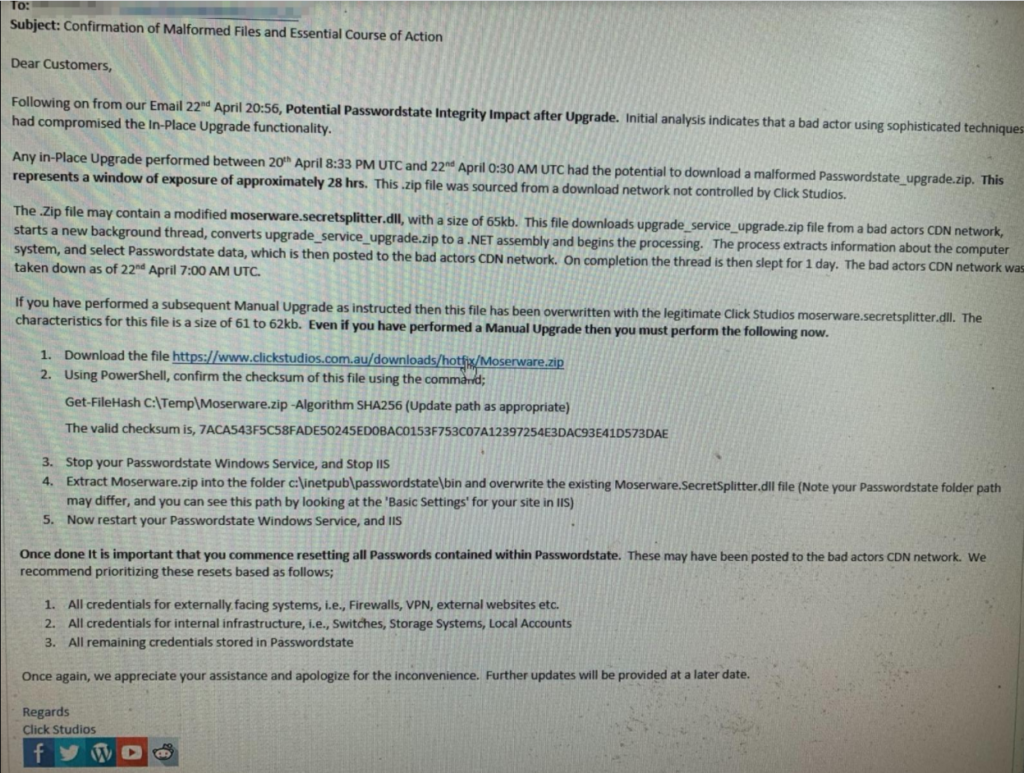
Furthermore, an email notification sent to customers on the supply chain attack malicious upgrades were potentially downloaded by customers between April 20 and April 22.
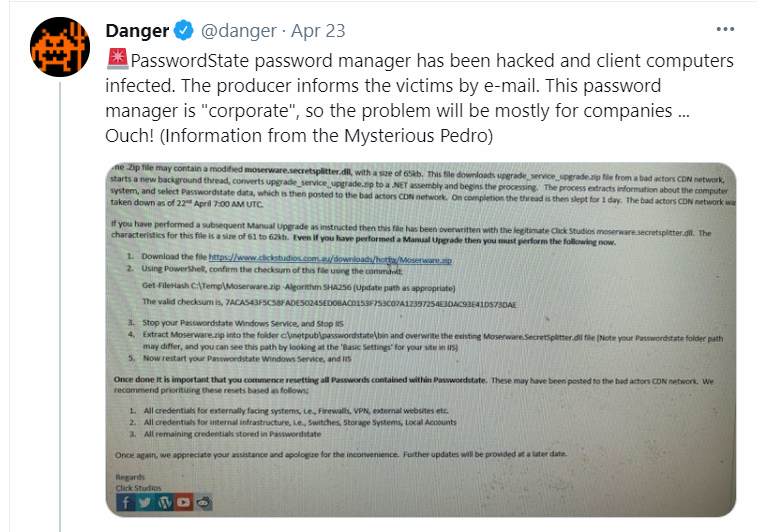
Also, Manual Upgrades of Passwordstate are not compromised. Affected customers password records may have been harvested.
Malformed Download
According to Click Studios, malformed Upgrade performed between 20th April 8:33 PM UTC and 22nd April 0:30 AM UTC — Passwordstate_ipgrade.zip [..]
Where the source not controlled by Click Studios, the company said.
On the other hand, a 4KB a ‘Loader’ code section added by threat actors from an older version to Passwordstate’s original code.
Info Harvested By Malware
The malware loaded has the functionality to pull a next stage payload from the C2.
But at the time of writing, the C&C is down, and unfortunately we didn’t manage to retrieve the 2nd stage payload, researchers said.
However, There’s also code to parse the ‘PasswordState‘ vault’s global settings (Proxy UserName/Password, etc).
Certainly, malware would collect information including:
- computer name
- user name
- domain name
- current process name
- current process id
- names, and IDs of all running processes
- names of all running services
- display name and status
- Passwordstate instance’s Proxy Server Address
- usernames, and passwords.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!
Importantly, users recommended to reset password by prioritizing as follows:
- credentials for Internet-exposed systems (firewalls, VPN, external websites, etc.)
- all credentials for internal infrastructure
- all remaining credentials
In short, Click Studios has released a hotfix package helping customers remove the attacker’s tampered DLL and overwrite it with a legitimate variant.
IOCs
Malicious dll:
f23f9c2aaf94147b2c5d4b39b56514cd67102d3293bdef85101e2c05ee1c3bf9
Moserware.SecretSplitter.dll
User-Agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.128 Safari/537.36
C&C:
- https://passwordstate-18ed2.kxcdn[.]com/upgrade_service_upgrade.zip
- passwordstate-18ed0.kxcdn[.]com
- passwordstate-18ed1.kxcdn[.]com
- passwordstate-18ed4.kxcdn[.]com
- passwordstate-18ed5.kxcdn[.]com
- passwordstate-8665.kxcdn[.]com







