
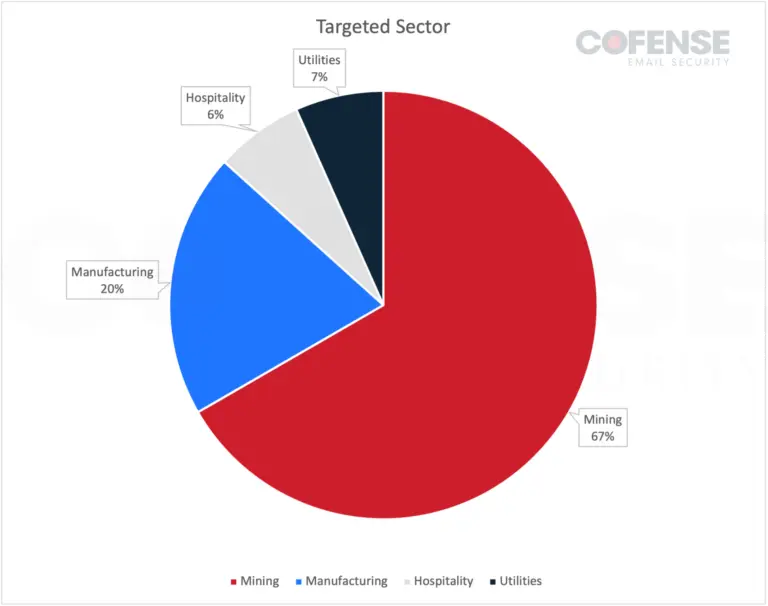
In early 2024, Cofense researchers discovered Poco RAT, a malware specifically targeting Spanish-speaking individuals in the mining industry. It spreads through Google Drive-hosted 7zip archives, effectively masking its malicious activities. By Q2 2024, Poco RAT had expanded its reach to multiple sectors, with a predominant focus remaining on mining.
Poco RAT
The malware features custom code that prioritizes basic RAT functionality over extensive monitoring or credential harvesting. Moreover, its attacks exhibit consistent Tactics, Techniques, and Procedures (TTPs).
Poco RAT is distributed through 7zip archives containing executables, delivered via three methods:
- Direct Google Drive URLs in emails (53%)
- Links embedded in HTML files (40%)
- Links within attached PDFs (7%)
These tactics exploit legitimate file hosting services to bypass Secure Email Gateways (SEGs).
The HTML method adds an additional layer of obfuscation by initially downloading an HTML file, which subsequently links to the malware.
Although the PDF method is the rarest, it’s potentially the most effective at evading detection, as SEGs often consider PDFs non-malicious and may miss embedded URLs.
Poco RAT utilizes POCO C++ libraries and is delivered as a Delphi-based executable. Despite extensive efforts to evade detection through metadata manipulation, it still faces average detection rates of 38% for executables and 29% for archives, highlighting its sophisticated evasion tactics.
The malware establishes persistence via registry keys, injects into the legitimate grpconv.exe process, and communicates with a C2 server at 94.131.119.126 on specific ports.
While its primary functions include gathering environment information, it can also download and execute additional malware, potentially leading to more severe compromises.
The malware employs well-known open-source libraries and legitimate processes to camouflage its activities within regular system operations.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




