
Hidden vulnerabilities in old Python code can create serious risks for today’s development environments.
A recent example involves legacy bootstrap scripts used by the zc.buildout tool. These outdated scripts still rely on hardcoded links to external domains that are no longer controlled by their original owners.
Impacted Python Packages
The main issue is that the script tries to download the old distribute package from python-distribute[.]org. That domain has been abandoned since 2014 and is now parked and available for anyone to buy.
If an attacker purchases the domain, they could host malicious files. Any developer using these old bootstrap scripts would unknowingly download and run the attacker’s code, making this a simple but dangerous attack path.
The problem creates a clear opening for supply-chain attacks because normal security checks are skipped entirely.
ReversingLabs researchers uncovered this flaw and found that it impacts several widely used packages such as slapos.core, pypiserver, and tornado.
Even though modern packaging standards have replaced these older methods, many projects still carry these legacy files in their repositories. That leftover code becomes a hidden risk.
This issue doesn’t appear during a regular pip install. Instead, it only becomes active when the old bootstrap script is run manually or triggered during a build process like a Makefile.
When it runs, the script trusts whatever comes from the abandoned domain, creating a major supply-chain threat—much like the fsevents compromise in the npm ecosystem.
Understanding How the Script Runs
The vulnerability comes from the unsafe way the bootstrap script tries to fetch and install dependencies. Its logic is designed to look for the old distribute package, and that check triggers the insecure download process.
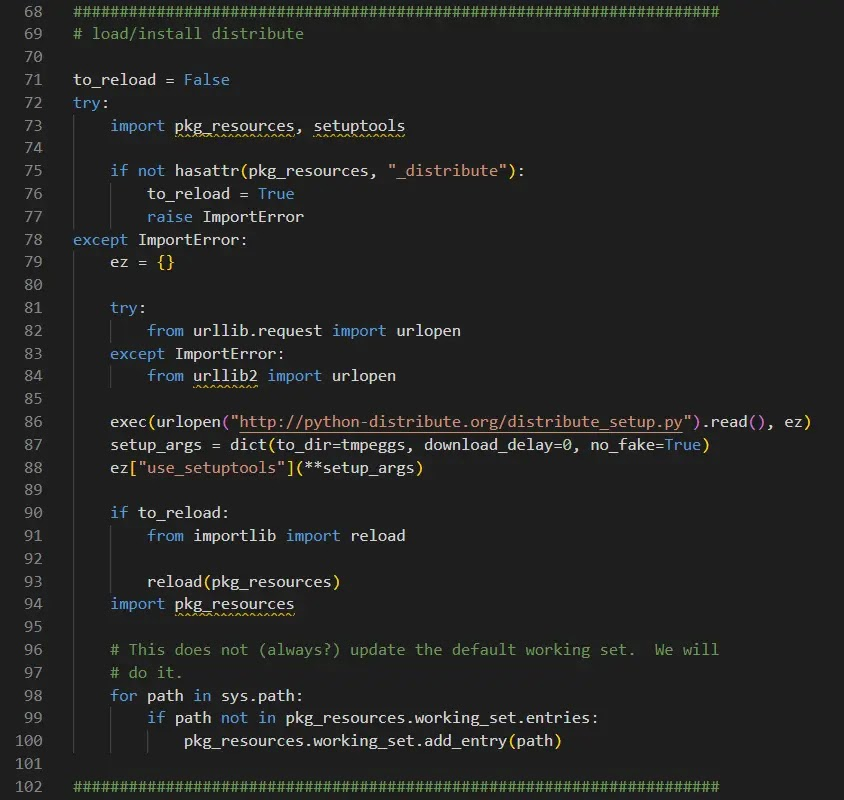
bootstrap.py code responsible for fetching and executing the distribute setup (ReversingLabs)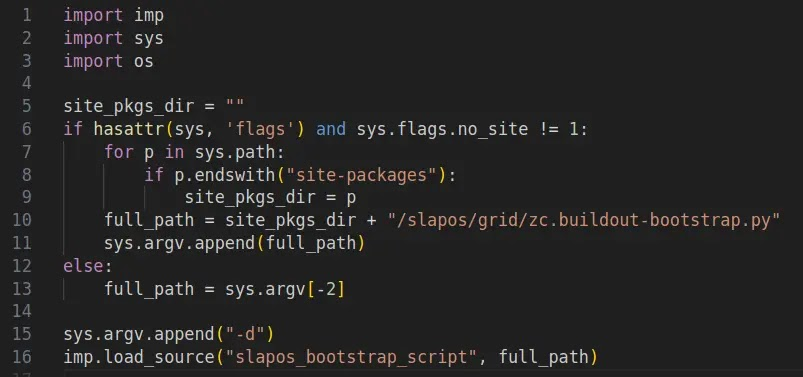
If the package isn’t found, the script starts a download process using Python’s urllib. As shown above, bootstrap.py fetches and runs the distribute setup directly from the abandoned python-distribute[.]org domain.
The real danger is that the script sends the downloaded content straight into an exec() call with no safety checks, no signatures, and no validation of what it’s running.
To confirm this risk, researchers created a proof-of-concept targeting slapos.core. Their PoC forces the script into the vulnerable download path by adjusting command-line arguments.
When executed, the terminal output shows that the script successfully reaches the external domain—proving that any code hosted there would run with the user’s full permissions.




