Raspberry Robin is a Windows worm discovered by cybersecurity researchers from Red Canary, the malware propagates through removable USB devices.
The malicious code uses Windows Installer to reach out to QNAP-associated domains and download a malicious DLL. The malware uses TOR exit nodes as a backup C2 infrastructure.
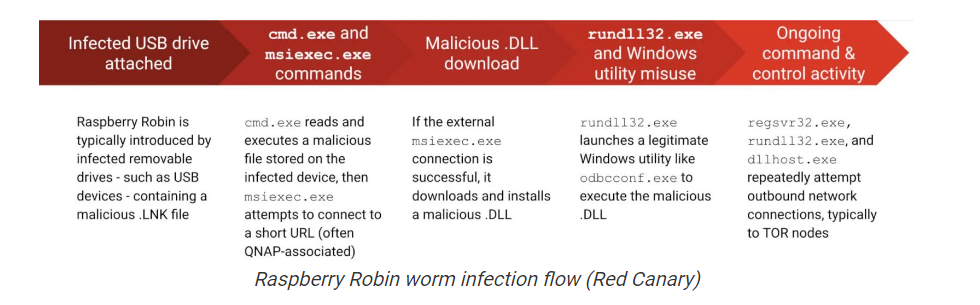
Raspberry Robin
The malware is spread via infected USB devices containing a .LNK file. As soon as a user clicks on this file, the worm creates an msiexec.exe process through Command Prompt and launches another malicious file. Then, it communicates with command and control servers with a short URL. If the connection is successful, it downloads and installs a bunch of other malicious DLLs, which then attempt to communicate with TOR nodes.
According to the researchers, looking for fodhelper.exe as a parent process it is possible to detect the threat.
It is important to note that Raspberry Robin is not a new piece of malware. It was first spotted by multiple security experts in 2021 and Microsoft even saw evidence of it being used back in 2019.
This is in spite of the fact that they could easily escalate their attacks. So that the malware can bypass User Account Control (UAC) on infected systems using legitimate Windows tools. However, Microsoft has tagged this campaign as high-risk.
File Hash
- e8f0d33109448f877a0e532b1a27131a
- 80f8291c0b707e1bf4c8d2fcb06e2101
- 94414cc9a9a7907bd7e7fbabc07e4421
Follow us for more, Facebook, Twitter, LinkedIn and Instagram













Leave A Comment