
X-Labs identified ransomware targeting Turkish businesses through PDF attachments in emails from the internet[.]ru domain. These PDFs contain links that download exe payloads, encrypting files with the “.shadowroot” extension. This ransomware is affecting global organizations, including healthcare and e-commerce sectors.
ShadowRoot Ransomware
A PDF attachment with a malicious URL linking to a compromised GitHub account has been identified as the initial access vector. This link downloads an executable payload named “PDF.FaturaDetay_202407.exe,” indicating potential malware delivery and system compromise.
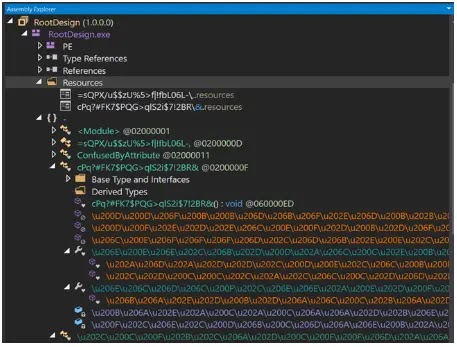
The analyzed 32-bit Borland Delphi 4.0 executable deploys secondary payloads—RootDesign.exe, Uninstall.exe, and Uninstall.ini—to the “C:\TheDream” directory. RootDesign.exe employs randomized class names, special characters, and obfuscated function names, protected by DotNet Confuser Core 1.6, to evade detection.
The primary executable uses PowerShell to discreetly execute RootDesign.exe, indicating potential malicious activity.
The command runs a hidden PowerShell script from “C:\TheDream\RootDesign.exe,” spawning multiple child processes and creating mutexes “Local\ZonesCacheCounterMutex,” “Local\ZonesLockedCacheCounterMutex,” and “_SHuassist.mtx.”
These processes replicate themselves recursively in memory, progressively consuming system resources.
At the same time, they encrypt non-PE and office files, replacing their extensions with “.ShadowRoot,” and log their actions in “C:\TheDream\log.txt” with the marker “ApproveExit.dot.”
According to ForcePoint, the ransomware uses the .NET AES cryptographic library for file encryption, repeatedly encrypting files through recursive self-propagation with RootDesign.exe. It displays Turkish ransom notes, demands cryptocurrency payment via email, and exfiltrates system data to a command-and-control server on smtp[.]mail[.]ru, port 587, using a compromised email account.

A novice attacker is targeting Turkish businesses with basic ransomware. Malicious PDF invoices download a Delphi payload that encrypts files as “.ShadowRoot” and communicates via a Russian SMTP server, indicating limited capabilities and inexperience.
Threat actors distribute malware via email from addresses including Kurumsal[.]tasilat[@]internet[.]ru, ran_master_som[@]proton[.]me, and lasmuruk[@]mailfence[.]com. The malware, identified by hashes CD8FBF0DCDD429C06C80B124CAF574334504E99A and 1C9629AEB0E6DBE48F9965D87C64A7B8750BBF93, is hosted at hxxps://raw[.]githubusercontent[.]com/kurumsaltahsilat/detayfatura/main/PDF.FaturaDetay_202407.exe.
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!





