
Elastic Security Labs has discovered a complex malware campaign, REF8685, targeting Iraq’s telecom sector. The campaign uses a new malware family, SHELBY, which exploits GitHub for command-and-control (C2), data exfiltration, and command retrieval.
SHELBY malware
The SHELBY malware family includes two key components: SHELBYLOADER and SHELBYC2.
The attack starts with a phishing email containing a malicious attachment (details.zip). When opened, it installs files in the %AppData%\Local\Microsoft\HTTPApi directory, including HTTPApi.dll (SHELBYC2) and HTTPService.dll (SHELBYLOADER).
SHELBYLOADER uses multiple techniques to evade detection, such as WMI queries, process enumeration, file system checks, and disk size analysis.
After execution, it ensures persistence by adding a registry entry and creates a unique identifier based on system-specific information.
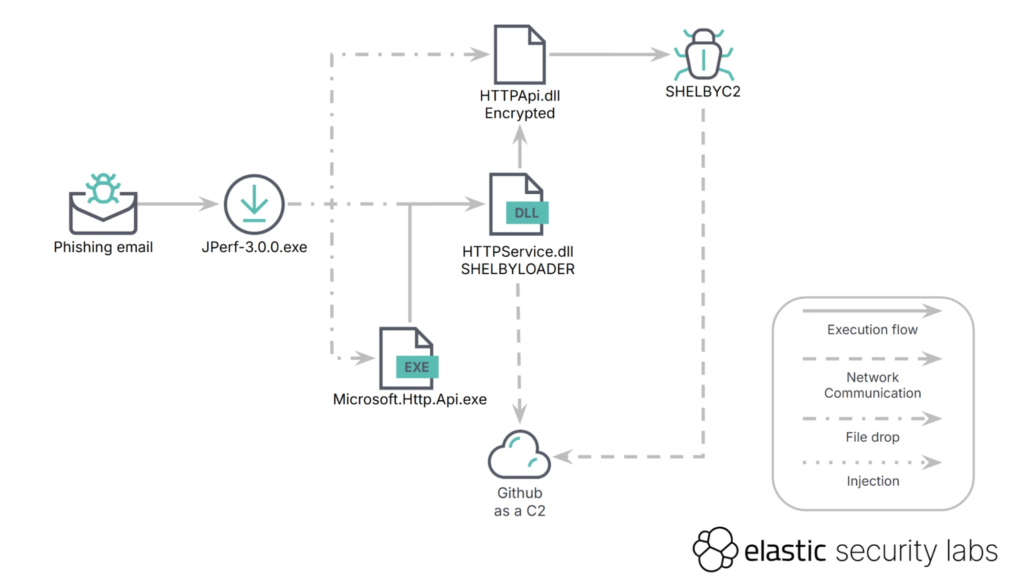
The malware’s command-and-control (C2) uses GitHub’s API with a private repository and a Personal Access Token (PAT) for authentication, bypassing standard Git tools.
SHELBYC2, the backdoor, is loaded into memory using reflection and decrypted with an AES key from a file downloaded from the C2 server. It supports commands like file download, upload, and loading additional .NET binaries.
The C2 design of the malware has a critical flaw: access to the Personal Access Token (PAT) could allow attackers to control infected machines or steal sensitive data, exposing victims to more risks.
The REF8685 campaign employs sophisticated social engineering, using compromised internal email accounts for convincing phishing attacks. The attackers have also targeted other entities, including an international airport in the UAE.
Elastic Security Labs has released YARA rules for detecting SHELBY malware variants. With signs of ongoing development, future updates may address current vulnerabilities and add new capabilities.
This campaign highlights the evolving tactics of threat actors, emphasizing the need for strong email security, employee training, and continuous network monitoring.
IOCs
| Observable | Type | Name | Reference |
|---|---|---|---|
0e25efeb4e3304815f9e51c1d9bd3a2e2a23ece3a32f0b47f829536f71ead17a | SHA-256 | details.zip | Lure zip file |
feb5d225fa38efe2a627ddfbe9654bf59c171ac0742cd565b7a5f22b45a4cc3a | SHA-256 | JPerf-3.0.0.exe | |
0354862d83a61c8e69adc3e65f6e5c921523eff829ef1b169e4f0f143b04091f | SHA-256 | HTTPService.dll | SHELBYLOADER |
fb8d4c24bcfd853edb15c5c4096723b239f03255f17cec42f2d881f5f31b6025 | SHA-256 | HTTPApi.dll | SHELBYC2 |
472e685e7994f51bbb259be9c61f01b8b8f35d20030f03215ce205993dbad7f5 | SHA-256 | JPerf-3.0.0.zip | Lure zip file |
5c384109d3e578a0107e8518bcb91cd63f6926f0c0d0e01525d34a734445685c | SHA-256 | Setup.exe | |
e51c6f0fbc5a7e0b03a0d6e1e1d26ab566d606b551c785bf882e9a02f04c862b | SHA-256 | Lure zip file | |
github[.]com/johnshelllby | URL | GitHub Account name – C2 | |
github[.]com/arturshellby | URL | GitHub Account name – C2 | |
arthurshelby[.]click | domain-name | DNS domain | |
speed-test[.]click | domain-name | ||
2.56.126[.]151 | ipv4 | ||
2.56.126[.]157 | ipv4 | ||
2.56.126[.]188 | ipv4 | ||
172.86.68[.]55 | ipv4 | ||
195.16.74[.]138 | ipv4 |
Follow Us on: Twitter, Instagram, Facebook to get the latest security news!




