Computer bug or virus malware found inside computer microprocessor unit or cpu, vulnerable network security system, 3d rendering low level hardware hacking attack data breaches concept
A critical flaw (CVE-2025-27090) in the Sliver C2 server allows attackers to hijack TCP connections using SSRF, enabling traffic interception and manipulation.
Sliver C2 Server Flaw
The vulnerability impacts Sliver C2 server versions from v1.5.26 to v1.5.42, as well as v1.6.0 before commit 0f340a2. Attackers can exploit this flaw to hijack TCP connections, intercept traffic, and manipulate data between compromised endpoints.
Any server installed since September 2022 may be at risk.
The SSRF exploit can expose teamserver IPs hidden behind redirectors and enable lateral movement within the network.
To exploit this vulnerability, an attacker needs access to a C2 port along with either a staging listener or a stager-generated implant binary.
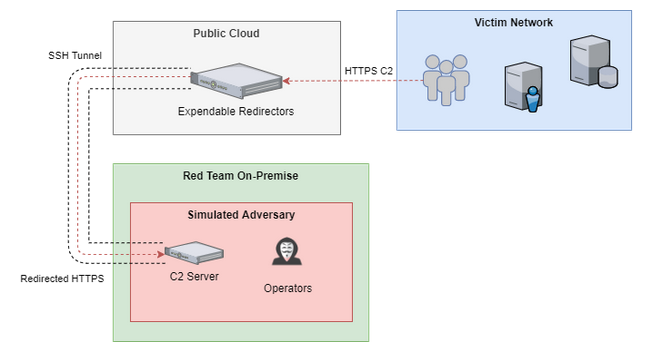
The exploit works by spoofing implant traffic to trick the teamserver into opening a TCP connection to any IP and port.
By altering the envelope type in implant traffic, attackers can trigger specific handler functions like registerSessionHandler and tunnelDataHandler.
Using registerSessionHandler, they can create a session and set up a reverse tunnel to hijack TCP traffic.
The tunnelDataHandler function is crucial, as it enables reverse tunnel creation. Attackers set the CreateReverse field to true and specify a target IP and port, forcing the teamserver to connect to an arbitrary endpoint.
Once established, this connection allows attackers to intercept, read, and manipulate network traffic.
Mitigation
- Update Sliver C2 servers to the latest patched version.
- Download the advisory and patched release to fix the SSRF vulnerability.
- Ensure all affected versions are updated promptly to prevent exploitation.
- Conduct regular security audits to maintain infrastructure integrity.




