A new malware campaign is actively targeting users in Brazil, using WhatsApp as the primary channel to deliver banking trojans and steal sensitive data. The operation combines social engineering, browser manipulation, and automated account abuse to spread quickly and discreetly.
The attackers begin by sending phishing emails containing archived VBS scripts. These scripts are heavily obfuscated to evade detection and serve as the first stage of the infection.Once executed, the payload installs Python and Selenium WebDriver components in the background.
These tools enable automated actions within WhatsApp Web, allowing the malware to interact with the platform without the victim’s knowledge.After setting up the environment, the malware injects malicious JavaScript into the victim’s browser session.
Through this injected code, it gains access to WhatsApp’s internal APIs, collects contact lists, and sends out malicious files to trusted contacts—making the campaign appear more credible.One of the most concerning aspects of this attack is that it does not require QR-code authentication. By copying existing browser cookies and local storage data, the malware hijacks logged-in WhatsApp Web sessions and abuses them to spread further.
K7 Security Labs has linked this malware variant to the larger Water-Saci campaign, a long-running operation targeting financial institutions across Brazil.
The infection chain uses a Python-based script to spread the malware and a banking trojan that watches for active Windows linked to Brazilian banks or cryptocurrency wallets.
By using automated messaging and loading parts of the malware directly into memory, the attackers keep the operation hidden while compromising both victims and their contact lists.
The campaign also drops an MSI installer, which includes an AutoIt script and encrypted payloads. This second stage sets up persistence through registry changes and keeps monitoring the victim’s screen for banking-related keywords.
When it detects a banking app or crypto wallet, the malware decrypts its trojan and runs it directly in memory, avoiding disk writes and evading standard file-based detection.
Technical Breakdown of the Infection Mechanism
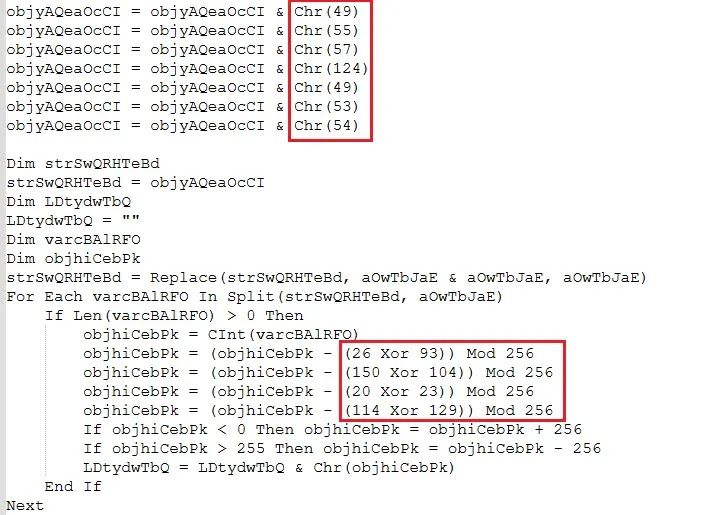
The attack begins with phishing emails that contain ZIP files. Inside these ZIPs is a VBS script that hides its real purpose using character encoding and XOR-based encryption to avoid being detected by antivirus tools.
The script is heavily obfuscated. Instead of writing commands directly, it builds them one character at a time using Chr() functions, then uses XOR operations to decode the hidden instructions.
In simple terms, the code slowly reconstructs the real malicious commands piece by piece, making it harder for security tools to understand or flag the script.
After the script is decoded, it downloads two files: an MSI installer and another VBS script. The second VBS file uses the same obfuscation tricks and then drops a batch file that installs Python, ChromeDriver, and Selenium.
This setup prepares everything needed to automate WhatsApp without any user action.
The main Python script, whats.py, then takes over the victim’s WhatsApp Web session. It does this by copying browser data—like cookies, local storage, and IndexedDB—into a temporary folder.
Using Selenium’s user-data-dir option, the script launches Chrome with these copied files. This allows the attacker to access WhatsApp Web without scanning a QR code, effectively hijacking the victim’s already logged-in session.
Once logged in, the malware loads JavaScript from GitHub into WhatsApp Web, giving it access to internal functions for reading contacts and sending messages.
It then collects the victim’s contacts—removing groups, business accounts, and filtered numbers—and sends them malicious ZIP files in batches. At the same time, it sends activity logs back to the attacker’s server.
Follow Us on: Linkedin, Instagram, Facebook to get the latest security news!